- Home
- About Journals
-
Information for Authors/ReviewersEditorial Policies
Publication Fee
Publication Cycle - Process Flowchart
Online Manuscript Submission and Tracking System
Publishing Ethics and Rectitude
Authorship
Author Benefits
Reviewer Guidelines
Guest Editor Guidelines
Peer Review Workflow
Quick Track Option
Copyediting Services
Bentham Open Membership
Bentham Open Advisory Board
Archiving Policies
Fabricating and Stating False Information
Post Publication Discussions and Corrections
Editorial Management
Advertise With Us
Funding Agencies
Rate List
Kudos
General FAQs
Special Fee Waivers and Discounts
- Contact
- Help
- About Us
- Search

The Open Cybernetics & Systemics Journal
(Discontinued)
ISSN: 1874-110X ― Volume 12, 2018
Watermark Detection in NSCT-Domain
Hongbo Bi*, Ying Liu, Yanliang Ge, Yubo Zhang , Mengmeng Wu
Abstract
In this paper, we presented a Rao hypothesis detector by modeling Cauchy distribution for the NonSubsampled Contourlet Transform (NSCT) subband coefficients in the field of additive spread spectrum image watermarking. Firstly, the NSCT subband coefficients were modeled following the Cauchy distributions. Secondly, a blind Rao test watermark detector was derived in the NSCT domain. Finally, the robustness of the proposed watermarking scheme was evaluated. Experimental results show that the proposed Rao detector guarantees the lowest probability of miss under the given probability of false alarm.
Article Information
Identifiers and Pagination:
Year: 2016Volume: 10
First Page: 1
Last Page: 12
Publisher Id: TOCSJ-10-1
DOI: 10.2174/1874110X01610010001
Article History:
Received Date: 10/06/2015Revision Received Date: 29/07/2015
Acceptance Date: 15/08/2015
Electronic publication date: 25/3/2016
Collection year: 2016
open-access license: This is an open access article licensed under the terms of the Creative Commons Attribution-Non-Commercial 4.0 International Public License (CC BY-NC 4.0) (https://creativecommons.org/licenses/by-nc/4.0/legalcode), which permits unrestricted, non-commercial use, distribution and reproduction in any medium, provided the work is properly cited.
* Address correspondence to this author at the School of Electrical Information Engineering, Northeast Petroleum University, Daqing 163318, China; E-mail:bihongbo@hotmail.com
| Open Peer Review Details | |||
|---|---|---|---|
| Manuscript submitted on 10-06-2015 |
Original Manuscript | Watermark Detection in NSCT-Domain | |
1. INTRODUCTION
In the past decades, watermarking has become one of the most active research fields and has received a great deal of attention not only in the academic community but also in the industry for its supply of an effective solution to the intellectual copyright protection for digital media.
Watermarking strategy is accomplished by embedding digital information (watermark) in original multimedia content (host), mostly without affecting the perceptual quality of original data greatly.
Additive watermarking in the transform domain is the simplest and commonly used way, since it can enhance the robustness against attacks or control the perceptive quality.
Many approaches for additive watermarks implemented in Discrete Cosine Transformation (DCT) domain, which can concentrate the whole energy of the host signal in fewer coefficients, have been proposed in literature so far [1J.R. Hernández, M. Amado, and F. Pérez-González, "DCT-domain watermarking techniques for still images: detector performance analysis and a new structure", IEEE Trans. Image Process., vol. 9, no. 1, pp. 55-68, 2000.
[http://dx.doi.org/10.1109/83.817598] [PMID: 18255372] , 2A. Nikolaidis, and I. Pitas, "Asymptotically optimal detection for additive watermarking in the DCT and DWT domains", IEEE Trans. Image Process., vol. 12, no. 5, pp. 563-571, 2003.
[http://dx.doi.org/10.1109/TIP.2003.810586] [PMID: 18237932] ]. Many directional image representations have been proposed in the recent years, which include the dual tree complex wavelets, bandlets, contourlets and NonSubsampled Contourlet Transform (NSCT) [3I.W. Selesnick, R.G. Baraniuk, and N.G. Kingsbury, "The dual-tree complex wavelet transform", IEEE Trans. Signal Process., vol. 22, no. 6, pp. 123-151, 2005.
[http://dx.doi.org/10.1109/MSP.2005.1550194] -6A.L. da Cunha, J. Zhou, and M.N. Do, "The nonsubsampled contourlet transform: theory, design, and applications", IEEE Trans. Image Process., vol. 15, no. 10, pp. 3089-3101, 2006.
[http://dx.doi.org/10.1109/TIP.2006.877507] [PMID: 17022272] ].
At the receiving end, watermark could be detected or extracted from watermarked (maybe attacked) images to declare the legal ownership. Blind watermark detection is a crucial part of a watermarking system and various optimal transform-based methods have been proposed in the literatures [7P. Comesaña, N. Merhav, and M. Barni, "Asymptotically optimum universal watermark embedding and detection in the high-SNR regime", IEEE Trans. Inf. Theory, vol. 56, no. 6, pp. 2804-2815, 2010.
[http://dx.doi.org/10.1109/TIT.2010.2046223] -10H. Sadreazami, M.O. Ahmad, and M.N. Swamy, "A study of multiplicative watermark detection in the contourlet domain using alpha-stable distributions", IEEE Trans. Image Process., vol. 23, no. 10, pp. 4348-4360, 2014.
[http://dx.doi.org/10.1109/TIP.2014.2339633] [PMID: 25051554] ].
Various models have been developed to account for non-Gaussian behavior of image statistics. For the additive watermarking problem, Generalized Gaussian Distribution (GGD) [11Q. Cheng, and T.S. Huang, "An additive approach to transform-domain information hiding and optimum detection structure", IEEE Trans. Multimed., vol. 3, no. 3, pp. 273-284, 2001.
[http://dx.doi.org/10.1109/6046.944472] , 12R. Kwitt, P. Meerwald, and A. Uhl, "Blind dt-cwt domain additive spread-spectrum watermark detection", In: Proceedings of 2009 16th International Conference on Digital Signal Processing, IEEE: Santorini, 2009, pp. 1-8.
[http://dx.doi.org/10.1109/ICDSP.2009.5201255] ] has been widely adopted in all these years by many researchers. Recently, Cauchy distribution, [13X. Yin, S. Peng, and X. Zhu, "Detection for multiplicative watermarking in DCT domain by cauchy model", Lect. Notes Comput. Sci., vol. 7043, pp. 173-183, 2011.
[http://dx.doi.org/10.1007/978-3-642-25243-3_14] , 14R. Kwitt, P. Meerwald, and A. Uhl, "Lightweight detection of additive watermarking in the DWT-domain", IEEE Trans. Image Process., vol. 20, no. 2, pp. 474-484, 2011.
[http://dx.doi.org/10.1109/TIP.2010.2064327] [PMID: 20699210] ] has been an alternative solution applicable to the same problem.
In this work, we first modeled the statistical property of NSCT coefficients using different distributions. Furthermore, we derived the Rao hypothesis test detector, which can give the better performance without any prior knowledge of the embedding strength factor. Finally, the robustness of the proposed watermarking scheme againstattacks was verified. The rest of the paper is organized as follows. In Section II, we give the overview of the model of watermarking from the view of the communication system and the asymptotically optimum detection is derived. We modeled the statistical modeling of the NSCT coefficients using different probability distribution functions in Section III. In Section IV, we derived the Rao statistics for Cauchy distribution and proposed detection statistics for additive watermarking. Section V is devoted to the evaluation of the performance of the proposed approach in terms of invisibility and robustness for various settings. Finally, the main contributions of this work are summarized in Section VI where some suggestions for future research are also outlined.
2. MODELING THE WATERMARKING SYSTEM
2.1. Modeling Watermarking as a Communication System
Some researchers modeled the watermarking as the communication system. Embedding watermark process is considered as the signal transmitter. The watermark can be seen as the signal to be transmitted, the host can be seen as the noise, any operations to the watermarking system (e.g. compression, noising, etc.) can be modeled as the communication channel, and the detection of the embedded watermark corresponds to the detection of signal with the presence of noise at the receiver in the communication scenario.
Fig. (1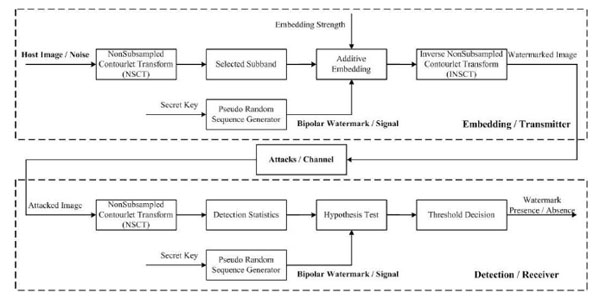 ) shows a schematic overview of the watermarking system configuration. Our emphasis is about the information detecting issue and in particular on blind detection of the transmitted watermark, which means we need to determine whether the watermark is present or not without reference to the original host information.
) shows a schematic overview of the watermarking system configuration. Our emphasis is about the information detecting issue and in particular on blind detection of the transmitted watermark, which means we need to determine whether the watermark is present or not without reference to the original host information.
 |
Fig. (1) Schematic overview of the watermarking system. |
In our configuration, the host data acts as the interference to the watermark signal. Hence, as for the signal detection, modeling the host signal is very crucial. Transform domains (such as the DWT domain, the Contourlet Transform domain and NSCT domain) facilitate selection of significant signal components and locations for embedding the watermark. We follow the additive embedding strategy throughout this paper, which has been researched in the literatures in the past few years and variety of detectors has been proposed which are based on the particular statistical model for the host transform coefficients [15A. Briassouli, P. Tsakalides, and A. Stouraitis, "Hidden messages in heavy-tails: DCT-domain watermark detection using alpha-stable models", IEEE Trans. Multimed., vol. 7, no. 4, pp. 700-715, 2005.
[http://dx.doi.org/10.1109/TMM.2005.850970] , 16N. Merhav, and E. Sabbag, "Optimal watermark embedding and detection strategies under limited detection resources", IEEE Trans. Inf. Theory, vol. 54, no. 1, pp. 255-274, 2008.
[http://dx.doi.org/10.1109/TIT.2007.911210] ].
2.2. Modeling Watermarking Detection as a Signal Detection Problem
To deduce the different signal detection strategies for additive spread spectrum watermarking scheme, we start with the classic Neyman-Pearson detection approach. It is worth noting that even we have the knowledge of the embedding strength at the detecting end, sometimes the host parameters are still unknown and have to be estimated from the received watermarked images. Therefore, we exploit the estimate-and-plug methods.
Suppose that the transform coefficients of the host are referred to as X1,X2, ... XN, which follow certain statistical distribution. For the additive spread spectrum watermarking, we assume that watermark W, denoted by W1,W2, ... WN, which follows an equally probable uniform distribution with bipolar values of {-1,+1}, so the corresponding probability function of can be written as
 |
(1) |
The watermark signal is generated by a Pseudo-Random Number Generator (PRNG) with a private seed as the secret key K. The rule for additive embedding can be formulated as
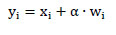 |
(2) |
Where α > 0 denotes the embedding strength and denotes yi the watermarked transform coefficients.
In terms of hypothesis testing, we can state the null-hypothesis (
 0) and alternative hypothesis (
0) and alternative hypothesis (
 1) as
1) as
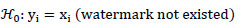 |
(3) |
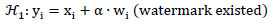 |
(4) |
Which is equivalent to the (two-sided) parameter test
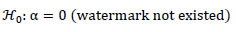 |
(5) |
 |
(6) |
In the rare case that the p.d.f.s (probability distribution functions) under both hypotheses can be completely specified, we can easily deduce a Neyman-Pearson (NP) detector which is optimal in the sense that it maximizes the probability of detection under a given probability of false alarm. Suppose that P(x; Θ
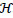 0) and P(x; Θ
0) and P(x; Θ
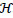 1) denote the p.d.f.s under
1) denote the p.d.f.s under
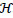 0 and
0 and
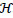 1, respectively, then according to the Neyman-Pearson criterion, we get the Likelihood Ratio Test (LRT) with threshold γ, which implies that the optimal detector favors
1, respectively, then according to the Neyman-Pearson criterion, we get the Likelihood Ratio Test (LRT) with threshold γ, which implies that the optimal detector favors
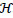 1 if
1 if
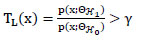 |
(7) |
The terms Θ
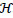 0 and Θ
0 and Θ
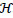 1 denote the fully specified parameter vector(s) of the noise model under
1 denote the fully specified parameter vector(s) of the noise model under
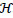 0 and
0 and
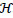 1, respectively.
1, respectively.
In case we can deduce the distribution of the detection statistic TL(X) under
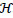 0, it is straight forward to determine a suitable threshold for a fixed probability of false alarm Pf as
0, it is straight forward to determine a suitable threshold for a fixed probability of false alarm Pf as
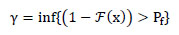 |
(8) |
Where ℱ(x) denotes the distribution function of TL(X) under
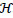 0.
0.
In order to constrain the probability of false alarm, the Neyman-Pearson test requires that the distribution of the detection statistic under
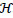 0 does not depend on any unknown parameters. However, as a matter of fact, the embedding strength α as well as the distribution parameters of the assumed host data model might be unknown to the detector. Therefore, it is more realistic that we have to estimate the unknown parameters from the received watermarked media.
0 does not depend on any unknown parameters. However, as a matter of fact, the embedding strength α as well as the distribution parameters of the assumed host data model might be unknown to the detector. Therefore, it is more realistic that we have to estimate the unknown parameters from the received watermarked media.
When we cannot completely specify the host data distribution under both hypotheses, we have to utilize the composite hypothesis testing approaches.
The Rao hypothesis test is a commonly used approach to solve the problem of composite hypothesis test.
The Rao test favors
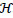 1 in case
1 in case
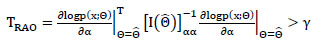 |
(9) |
Where
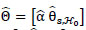 denotes the ML estimates under,
denotes the ML estimates under,
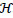 0, e.g.
0, e.g.
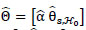 for a general parameter vector. Further, the term
for a general parameter vector. Further, the term
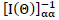 is given by
is given by
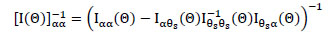 |
(10) |
Where 1α α, 1αθs, 1θs α and 1θs θs denote the partitions of the Fisher information matrix, which are defined by
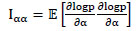 |
(11) |
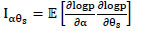 |
(12) |
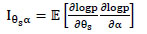 |
(13) |
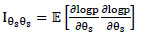 |
(14) |
It is well-known that the detection statistic TRAO asymptotically follows
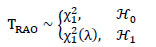 |
(15) |
Where X21 denotes a Chi-Square distribution with one degree of freedom and X21(λ) denotes a non-central Chi-Square distribution with one degree of freedom and non-centrality parameter λ
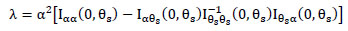 |
(16) |
We see that the Rao test leads to a Constant False-Alarm Rate (CFAR) detector since the detection statistic distribution under
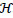 0 does not depend on any parameters, which avoids parameters estimation of the embedding strength α. Hence, no matter what host data model we construct, the threshold needs to be calculated only once, resulting in decrease of the computational efforts.
0 does not depend on any parameters, which avoids parameters estimation of the embedding strength α. Hence, no matter what host data model we construct, the threshold needs to be calculated only once, resulting in decrease of the computational efforts.
3. MODELING THE NSCT SUBBAND COEFFICIENTS AS STATISTICAL DISTRIBUTION
Non subsampled Contourlet Transform (NSCT) is a flexible multi-scale, multi-directional, and shift-invariant version for images representation originated from Contourlet Transform.
We discuss the statistical models of NSCT coefficients, and in particular, we take a closer look into the characteristic distributions which arise in some cases of natural images.
Fig. (2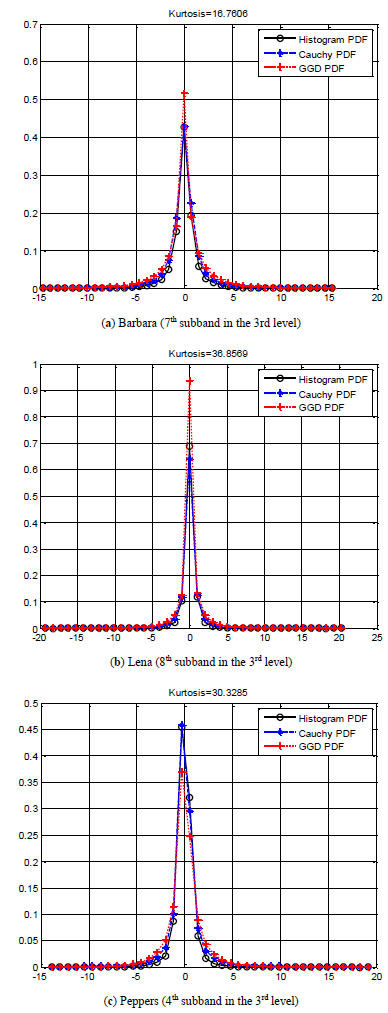 ) illustrates the histogram of finest subband coefficients of NSCT. As we can see, the coefficients are distributed with sharp peak at zero point and heavy tails at each side of the peak. Fig. (2
) illustrates the histogram of finest subband coefficients of NSCT. As we can see, the coefficients are distributed with sharp peak at zero point and heavy tails at each side of the peak. Fig. (2 ) also shows the corresponding p.d.f.s of fitted GGDs and Cauchy p.d.f.s to the same NSCT subband coefficients.
) also shows the corresponding p.d.f.s of fitted GGDs and Cauchy p.d.f.s to the same NSCT subband coefficients.
As illustrated by the visual GoF in Fig. (2 ), we conclude the Cauchy distribution can be the better choice for modeling the NSCT subband coefficients compared to the GGD.
), we conclude the Cauchy distribution can be the better choice for modeling the NSCT subband coefficients compared to the GGD.
4. HYPOTHESIS TEST DETECTOR FOR NSCT SUBBAND COEFFICIENTS
4.1. Rao Hypothesis Test Detector for NSCT Subband Coefficients following Cauchy Distribution
Nikolaidis et al. derived a watermark detector for additive spread spectrum watermarks exploiting Rao test in the DWT domain, which considered DWT coefficients as GGD variants [2A. Nikolaidis, and I. Pitas, "Asymptotically optimal detection for additive watermarking in the DCT and DWT domains", IEEE Trans. Image Process., vol. 12, no. 5, pp. 563-571, 2003.
[http://dx.doi.org/10.1109/TIP.2003.810586] [PMID: 18237932] ].
One of our main contributions is to derive a suboptimal watermark detector for host signal following Cauchy distribution, resulting in less computation for the ML estimation of the parameters and no need for the presence of embedding strength on the receiving end.
As we verified before, the Cauchy distribution is a reasonable model for NSCT subband coefficients. Furthermore, its parameter estimation can be performed efficiently.
In the first step, we derive the first term of the detection statistic in equation (9) and plug in the p.d.f. of the Cauchy distribution of equation
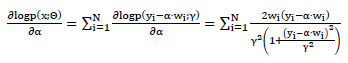 |
(17) |
and
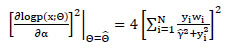 |
(18) |
Plugging in the ML estimate under
 0, we get the second term
0, we get the second term
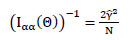 |
(19) |
Then, we combine above results, and get the following expression for the detection statistic of Rao hypothesis test conditioned on Cauchy host signal
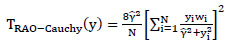 |
(20) |
4.2. Other Hypothesis Test Detectors
Similarly, we derived some other commonly used hypothesis test detectors.
Rao with Generalized Gaussian Distribution (Rao-GGD)
Nikolaidis et al. first proposed to use a Rao hypothesis test to replace the LRT detector [2A. Nikolaidis, and I. Pitas, "Asymptotically optimal detection for additive watermarking in the DCT and DWT domains", IEEE Trans. Image Process., vol. 12, no. 5, pp. 563-571, 2003.
[http://dx.doi.org/10.1109/TIP.2003.810586] [PMID: 18237932] ]. The detection statistic of Rao test assuming GGD host signal is given by
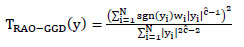 |
(21) |
LRT with Generalized Gaussian Distribution (LRT-GGD)
This detector was introduced by Hernández et al. based on the LRT and a Generalized Gaussian host signal noise model [1J.R. Hernández, M. Amado, and F. Pérez-González, "DCT-domain watermarking techniques for still images: detector performance analysis and a new structure", IEEE Trans. Image Process., vol. 9, no. 1, pp. 55-68, 2000.
[http://dx.doi.org/10.1109/83.817598] [PMID: 18255372] ]. The detection statistic is given by
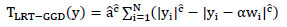 |
(22) |
 |
Fig. (2) Good of fitness for NSCT subband coefficients. |
Where the distribution parameters and are estimated from the received signal without caring whether a watermark is present or not.
LRT with Cauchy Distribution (LRT-Cauchy)
This detector was introduced by Briassouli et al. asan extension of the LRT-GGD detector [15A. Briassouli, P. Tsakalides, and A. Stouraitis, "Hidden messages in heavy-tails: DCT-domain watermark detection using alpha-stable models", IEEE Trans. Multimed., vol. 7, no. 4, pp. 700-715, 2005.
[http://dx.doi.org/10.1109/TMM.2005.850970] ]. The host signal noise is modeled by a Cauchy distribution and the detection statistic is given as
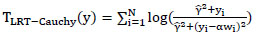 |
(23) |
From the derived detection statistics, we can see that the Rao detector does not need the information about embedding strength, as we declared before, which simplifies the realization of blind detecting the watermark.
5. EXPERIMENTAL RESULTS
To evaluate a comparative performance of various detectors for additive image watermarking in NSCT domain, a great deal of experiments with different images have been carried out to investigate the imperceptibility of the embedded watermark as well as the robustness of the proposed method against attacks. We embedded the watermark with the same size as the host images, which come from the standard image datasets of 256*256 bits. As a result, the watermark is 65536-bitlong.
We implement the following detectors combination for additive spread spectrum watermarking: the naming convention is that the first part of the name denotes the type of hypothesis test and the second part denotes the host signal statistical model.
First of all, we test the visual quality of the watermarked images, as listed in Table 1.
As we can see, the PSNRs are rather high. The images are indistinguishable with high PSNR values, thus showing the effectiveness of the additive NSCT watermarking in terms of the invisibility of the watermark.
Secondly, we analyze the performance of our detectors in the absence of attacks. (see Fig. 3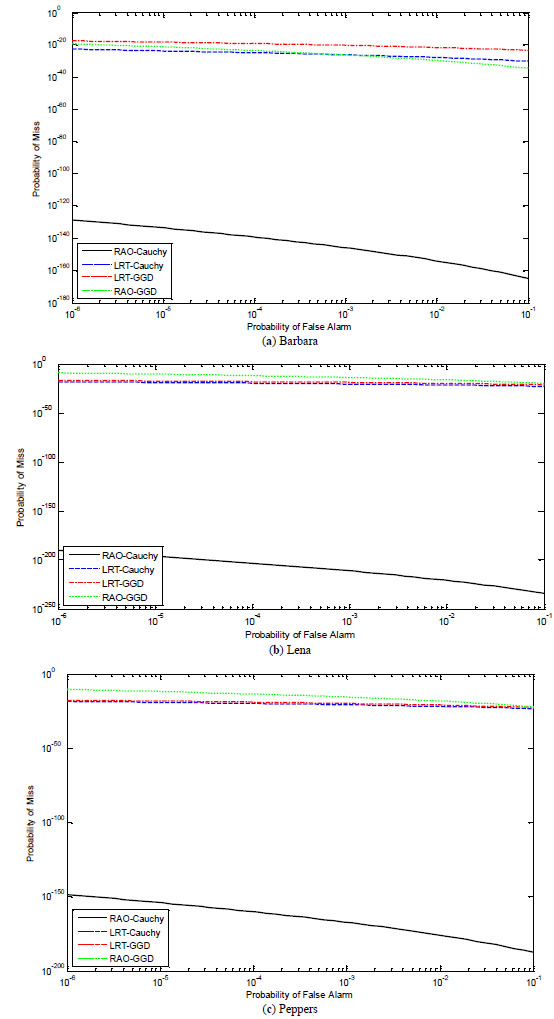 ). We determine the experimental receiver operating characteristics (ROC) curves by running 1000 randomly generated watermarks (simulating the
). We determine the experimental receiver operating characteristics (ROC) curves by running 1000 randomly generated watermarks (simulating the
 1 hypothesis).
1 hypothesis).
We examined the performance of ROC, where probability of miss varies with the probability of false alarm. It should be noted that the probability of miss is expected to be kept at a relatively low level for a predefined probability of false alarm to increase the reliability of detection.
It is seen that the Rao detector with Cauchy distribution yields a performance which is much better than others as evidenced by a lower probability of miss for any given value of false alarm.
The image received by the watermark detector might have been subjected to image processing operations. Consequently, we analyzed the robustness of the detectors against various attacks using the same set of images. Similarly, we determine the experimental ROC curves by running 1000 randomly generated watermarks.
The robustness of the proposed detector under JPEG compression is now investigated and the watermarked images are compressed by JPEG with compression quality factor of 70. Fig. (4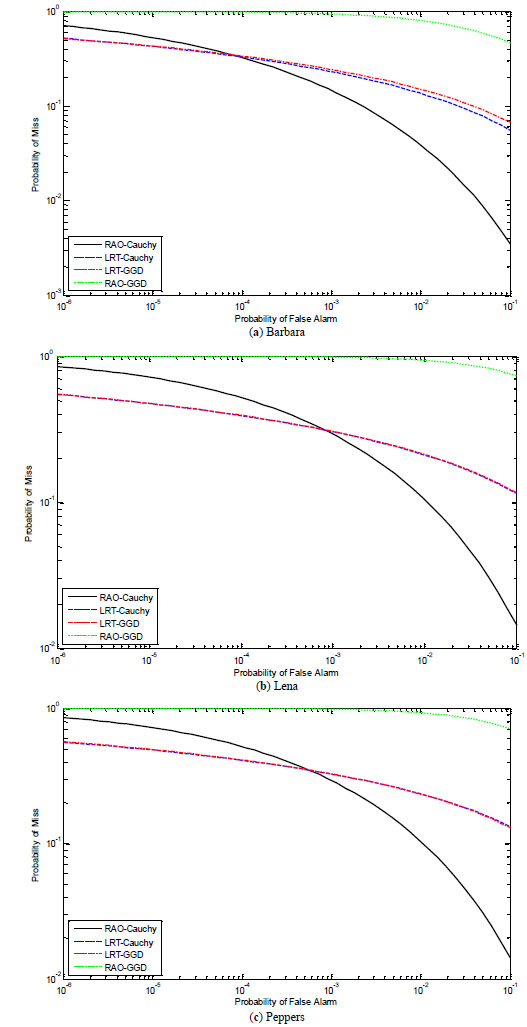 ) shows the averaged ROC curves obtained using various detectors.
) shows the averaged ROC curves obtained using various detectors.
The figure shows that the proposed Rao-Cauchy detectors are slightly less robust than LRT-Cauchy and LRT-GGD at the low level of probability of miss, but more robust against JPEG compression than the others at much higher level probability of miss, especially when it is higher than 10-3.
The performance against the random noise attack is also tested. Fig. (5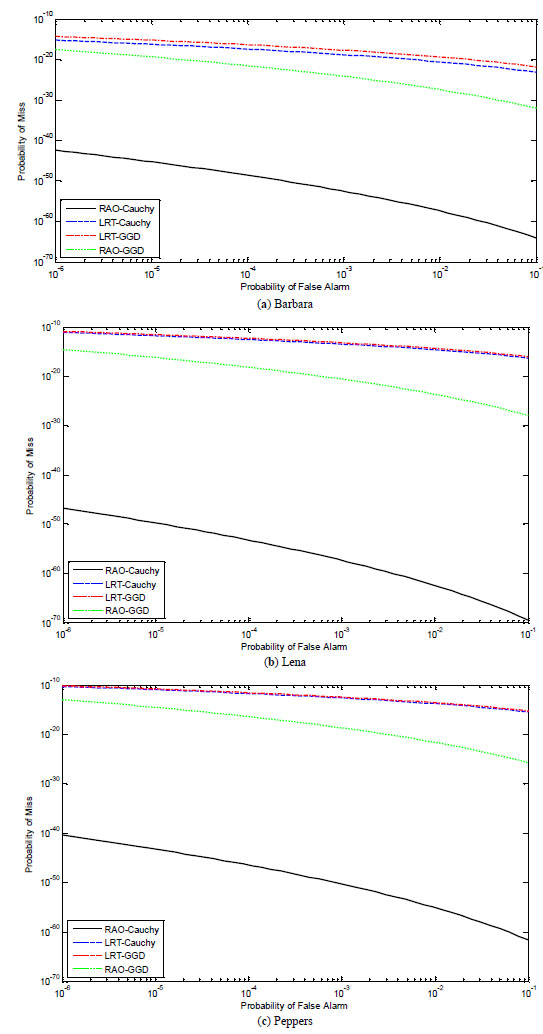 ) shows the averaged ROC curves for various detectors.
) shows the averaged ROC curves for various detectors.
 |
Fig. (3) Performance evaluation of ROC. |
 |
Fig. (4) Performance evaluation of ROC under JPEG compression attack with the quality of 70. |
 |
Fig. (5) Performance evaluation of ROC under random noise attack with 10. |
Fig. (5 ) shows that the proposed Rao-Cauchy detectors are much more robust against random noise than the others by providing lower probability of miss also.
) shows that the proposed Rao-Cauchy detectors are much more robust against random noise than the others by providing lower probability of miss also.
From all of results mentioned above, we conclude that the Rao hypothesis test for NSCT subband coefficients following Cauchy statistical distribution model might be more robust and a better choice for detecting the additive spread spectrum image watermarking.
CONCLUSION
In this paper, we proposed a blind detection approach for additive spread spectrum image watermarking scheme in the NSCT domain.
We first studied the suitability of the statistical distributions in modeling the NSCT coefficients of an image. The results show that the Cauchy distribution provides a more accurate fitting to the NSCT subband coefficients through a visual comparison to GGD.
Motivated by these modeling results, blind additive spread spectrum watermark detector in the NSCT domain following Cauchy distributions was designed.
The performance of the proposed detector has been evaluated in detail by conducting several experiments. The robustness of the proposed detector, using the Rao hypothesis and Cauchy p.d.f.s, against JPEG compression, random noise has been investigated and results show that the proposed detector is superior to that of other approaches.
CONFLICT OF INTEREST
The authors confirm that this article content has no conflict of interest.
ACKNOWLEDGEMENTS
This work is supported by the Heilongjiang Provincial Natural Science Foundation for Young Scholars under Grant No.QC2014C066.
REFERENCES
| [1] | J.R. Hernández, M. Amado, and F. Pérez-González, "DCT-domain watermarking techniques for still images: detector performance analysis and a new structure", IEEE Trans. Image Process., vol. 9, no. 1, pp. 55-68, 2000. [http://dx.doi.org/10.1109/83.817598] [PMID: 18255372] |
| [2] | A. Nikolaidis, and I. Pitas, "Asymptotically optimal detection for additive watermarking in the DCT and DWT domains", IEEE Trans. Image Process., vol. 12, no. 5, pp. 563-571, 2003. [http://dx.doi.org/10.1109/TIP.2003.810586] [PMID: 18237932] |
| [3] | I.W. Selesnick, R.G. Baraniuk, and N.G. Kingsbury, "The dual-tree complex wavelet transform", IEEE Trans. Signal Process., vol. 22, no. 6, pp. 123-151, 2005. [http://dx.doi.org/10.1109/MSP.2005.1550194] |
| [4] | E. Le Pennec, and S. Mallat, "Sparse geometric image representations with bandelets", IEEE Trans. Image Process., vol. 14, no. 4, pp. 423-438, 2005. [http://dx.doi.org/10.1109/TIP.2005.843753] [PMID: 15825478] |
| [5] | M.N. Do, and M. Vetterli, "The contourlet transform: an efficient directional multiresolution image representation", IEEE Trans. Image Process., vol. 14, no. 12, pp. 2091-2106, 2005. [http://dx.doi.org/10.1109/TIP.2005.859376] [PMID: 16370462] |
| [6] | A.L. da Cunha, J. Zhou, and M.N. Do, "The nonsubsampled contourlet transform: theory, design, and applications", IEEE Trans. Image Process., vol. 15, no. 10, pp. 3089-3101, 2006. [http://dx.doi.org/10.1109/TIP.2006.877507] [PMID: 17022272] |
| [7] | P. Comesaña, N. Merhav, and M. Barni, "Asymptotically optimum universal watermark embedding and detection in the high-SNR regime", IEEE Trans. Inf. Theory, vol. 56, no. 6, pp. 2804-2815, 2010. [http://dx.doi.org/10.1109/TIT.2010.2046223] |
| [8] | A. Mairgiotis, L. Kondi, and Y. Yang, "Locally optimum detection for additive watermarking in the DCT and DWT domains through non-Gaussian distributions", In: Proceedings of 2013 18th International Conference on Digital Signal Processing, IEEE: Santorini, 2013, pp. 1-6. [http://dx.doi.org/10.1109/ICDSP.2013.6622794] |
| [9] | M. Mundher, D. Muhamad, A. Rehman, T. Saba, and F. Kausar, "Digital watermarking for images security using discrete slantlet transform", Appl. Math. Inf. Sci., vol. 8, no. 6, pp. 2823-2830, 2014. [http://dx.doi.org/10.12785/amis/080618] |
| [10] | H. Sadreazami, M.O. Ahmad, and M.N. Swamy, "A study of multiplicative watermark detection in the contourlet domain using alpha-stable distributions", IEEE Trans. Image Process., vol. 23, no. 10, pp. 4348-4360, 2014. [http://dx.doi.org/10.1109/TIP.2014.2339633] [PMID: 25051554] |
| [11] | Q. Cheng, and T.S. Huang, "An additive approach to transform-domain information hiding and optimum detection structure", IEEE Trans. Multimed., vol. 3, no. 3, pp. 273-284, 2001. [http://dx.doi.org/10.1109/6046.944472] |
| [12] | R. Kwitt, P. Meerwald, and A. Uhl, "Blind dt-cwt domain additive spread-spectrum watermark detection", In: Proceedings of 2009 16th International Conference on Digital Signal Processing, IEEE: Santorini, 2009, pp. 1-8. [http://dx.doi.org/10.1109/ICDSP.2009.5201255] |
| [13] | X. Yin, S. Peng, and X. Zhu, "Detection for multiplicative watermarking in DCT domain by cauchy model", Lect. Notes Comput. Sci., vol. 7043, pp. 173-183, 2011. [http://dx.doi.org/10.1007/978-3-642-25243-3_14] |
| [14] | R. Kwitt, P. Meerwald, and A. Uhl, "Lightweight detection of additive watermarking in the DWT-domain", IEEE Trans. Image Process., vol. 20, no. 2, pp. 474-484, 2011. [http://dx.doi.org/10.1109/TIP.2010.2064327] [PMID: 20699210] |
| [15] | A. Briassouli, P. Tsakalides, and A. Stouraitis, "Hidden messages in heavy-tails: DCT-domain watermark detection using alpha-stable models", IEEE Trans. Multimed., vol. 7, no. 4, pp. 700-715, 2005. [http://dx.doi.org/10.1109/TMM.2005.850970] |
| [16] | N. Merhav, and E. Sabbag, "Optimal watermark embedding and detection strategies under limited detection resources", IEEE Trans. Inf. Theory, vol. 54, no. 1, pp. 255-274, 2008. [http://dx.doi.org/10.1109/TIT.2007.911210] |




