- Home
- About Journals
-
Information for Authors/ReviewersEditorial Policies
Publication Fee
Publication Cycle - Process Flowchart
Online Manuscript Submission and Tracking System
Publishing Ethics and Rectitude
Authorship
Author Benefits
Reviewer Guidelines
Guest Editor Guidelines
Peer Review Workflow
Quick Track Option
Copyediting Services
Bentham Open Membership
Bentham Open Advisory Board
Archiving Policies
Fabricating and Stating False Information
Post Publication Discussions and Corrections
Editorial Management
Advertise With Us
Funding Agencies
Rate List
Kudos
General FAQs
Special Fee Waivers and Discounts
- Contact
- Help
- About Us
- Search

The Open Cybernetics & Systemics Journal
(Discontinued)
ISSN: 1874-110X ― Volume 12, 2018
A Research for Cloud Computing Security Risk Assessment
Hua Tang*, 1, 2, Jiejun Yang1, 3, Xiaofang Wang1, Qi Zhou4
Abstract
In order to solve the problem of the complexity of the process and the accuracy of evaluation results in cloud computing security risk assessment, the hierarchical holographic modeling method is applied to cloud computing risk identification phase, so as to clearly capture the cloud computing risk factors through a comprehensive analysis of cloud computing security domains. Moreover, with cloud computing security factors as the basic unit, fuzzy set theory and entropy weight method are used to accurately quantify the probability of cloud computing security risks and the resulting losses for a comprehensive assessment of cloud computing security risks. Finally, an example is given for calculation and verification, and the deficiencies of cloud computing security risk assessment are analyzed.
Article Information
Identifiers and Pagination:
Year: 2016Volume: 10
First Page: 210
Last Page: 217
Publisher Id: TOCSJ-10-210
DOI: 10.2174/1874110X01610010210
Article History:
Received Date: 19/05/2016Revision Received Date: 08/09/2016
Acceptance Date: 09/09/2016
Electronic publication date: 31/10/2016
Collection year: 2016
open-access license: This is an open access article licensed under the terms of the Creative Commons Attribution-Non-Commercial 4.0 International Public License (CC BY-NC 4.0) (https://creativecommons.org/licenses/by-nc/4.0/legalcode), which permits unrestricted, non-commercial use, distribution and reproduction in any medium, provided the work is properly cited.
Correspondence: Address correspondence to this author at the Information Technology Center, Hubei University of Technology, Wuhan, Hubei, 430068, China; Tel: +86 27 59750810; Fax: +86 27 59750815; E-mails: th@mail.hbut.edu.cn, tanghua_2008@163.com
| Open Peer Review Details | |||
|---|---|---|---|
| Manuscript submitted on 19-05-2016 |
Original Manuscript | A Research for Cloud Computing Security Risk Assessment | |
1. INTRODUCTION
In June 2008, the world-famous research firm Gartner issued a report “Assessing the Security Risks of Cloud Computing” in which cloud computing security risks have been studied for the first time from the perspective of risk management with specific elaboration on seven risks such as user access, regulatory compliance, and so on. In April 2009, the nonprofit organization Cloud Security Alliance (CSA) released “Security Guidance for Critical Areas of Focus in Cloud Computing” which promotes the best practice of cloud computing security in a standardized form. As cloud computing security issues become increasingly prominent, research on cloud computing security risk theories has received increasing concern in the industry and academics. Neela, K. L. et al. analyzed the security risks, threats, and the impact on different users of cloud computing [1K.L. Neela, V. Kavitha, and R.K. Ramesh, "Cloud computing: Threats and security issues", Int. J. Engi. Sci. Res. Tech., vol. 2, no. 8, pp. 2070-2072, 2013.]. Latif R. et al. elaborated the risk factors of cloud users/business organization cloud environment and mapped them as the actual needs of cloud users / business organization [2R. Latif, H. Abbas, S. Assar, and Q. Ali, "Cloud Computing Risk Assessment: A Systematic Literature Review", In: J.J. Park, I. Stojmenovic, M. Choi, and F. Xhafa, Eds., Future Information Technology, vol. 276. Germany Springer Publishers, Verlag: Berlin, 2014, pp. 285-295.]. Considering all kinds of security risk factors provided by cloud computing risk management decision support system, Fan C.K. et al. adopted a model algorithm to complete the identification and analysis of the losses resulting from cloud computing risks, and maintained social engineering, cross-cloud compatibility, and mistakes made by employees as high risk factors in a variety of cloud applications [3C.K. Fan, and T.C. Chen, "The risk management strategy of applying cloud computing", Int. J. Adv. Comp. Sci. App., vol. 3, no. 9, pp. 18-27, 2012.]. By exploring a variety of risks in cloud computing, Schllings C. and Simon S. used risk breakdown structure (RBS) from the perspective of cloud users and proposed specific measures and recommendations based on the analysis and evaluation of the extracted risk factors [4C. Schllings, and S. Simom, "Risk Management on the Security Problem in Cloud Computing", In: First ACIS/JNU International Conference on Computer, Networks, System and Industrial Engineering, 2011, pp. 147-152.]. Through designing a cloud computing security risk assessment model, Wang H.B. et al. put forward a specific risk assessment method, with which the vulnerability of security management in cloud computing environment was revealed effectively in the experimental environment [5H.B. Wang, F. Liu, and H. Liu, "A Method of the Cloud Computing Security Management Risk Assessment", In: D.H. Zeng, Ed., Advances in Intelligent and Soft Computing, vol. 141. Germany Springer Publishers, Verlag: Berlin, 2012, pp. 609-618.]. Using standards such as ISO 27005, NIST SP800-30 and AS/NZS 4360, Albakri S. H. et al. presented a security risk assessment framework which allows not only cloud service providers’ assessment on security risks in cloud computing environment but also cloud customers’ contribution to risk assessment. Through cloud clients’ evaluation on the security risk factors, the framework can provide a more realistic and accurate risk assessment, and thereby reduce the complexity of customer participation in the process of risk assessment [6S.H. Albakri, B. Shanmugam, G.N. Samy, N.B. Ldris, and A. Ahmed, "Security risk assessment framework for cloud computing environments", Security Com. Netw., vol. 7, no. 11, pp. 2114-2124, 2014.
[http://dx.doi.org/10.1002/sec.923] ].
2. THE CONNOTATION OF CLOUD COMPUTING SECURITY RISK ASSESSMENT
According to the theory of risk management, cloud computing security risk assessment involves cloud computing security risk identification, risk calculation and other processes so as to effectively meet the requirements of cloud computing in the SLA commitment and QoS constraint service selection. Firstly, cloud computing related assets, such as cloud infrastructure, computing resources, application software, and cloud users, and threats to these assets are listed and organized into risk source table to identify the main risk factors through the corresponding risk identification model. Secondly, the probability of risk occurrence resulting from cloud computing threats and vulnerabilities is calculated according to related theories and methods and the “high probability” of cloud computing security risk consequences is inferred. Meanwhile, under certain conditions, the extent of potential losses is relatively accurately calculated and cloud computing security risk level is determined so as to provide support for cloud computing service providers, cloud users and regulators in risk decision-making and implementation.
Concerning domestic and international academic and industrial world, the theory and practice of cloud computing security started late, research on cloud computing security risk assessment is even scarcer. There are two major problems: one is the lack of systematic research on the whole process of cloud computing security risk assessment with either focus on cloud computing security risk analysis or risk calculation; the other is the tendency of qualitative research rather than quantitative research which, if any, is only applied to some specific areas (such as storage resources).
3. CLOUD COMPUTING SECURITY RISK ASSESSMENT
3.1. Identification of Cloud Computing Security Risks
The components of cloud computing (as a pay-per-use model) can not only be allocated, deployed and recovered quickly, but also reduced or expanded swiftly. This high scalability and flexibility has brought considerable convenience and benefits for users, but also many difficulties in cloud computing security risk management, especially in risk identification. In Hierarchical Holographic Modeling (HHM), with the system as the research object, the inherent nature is displayed through a multi-angle and multi-dimensional analysis in the form of a chart framework. In order to obtain a full understanding of large-scale systems and reveal the essential characteristics of the system, HHM divides the large and complex system into different classifications from different angles and aspects. Each classification can only describe the relevant content and attributes of a certain aspect of the hierarchical system which break down in a stepwise manner until the last breakdown.
HHM method is suitable for solving large-scale complex problems. Considering the complexity, randomness and uncertainty of security risk identification of cloud computing, with the application of HHM, the definition and identification according to the background reasons, characteristics and expected consequences of cloud computing security risks, and the hierarchical classification of all risk factors, cloud computing system can be described hierarchically from different perspectives and comprehensive security risk identification and inherent relationship between different risk factors can be organized effectively [7T.P. Chen, L.J. Zheng, and X.Y. Zhang, "Application of HHM in risk identification of information system", J. Safety Sci. Tech., vol. 4, no. 6, pp. 98-100, 2008.]. The major steps are as follows:
I. Compilation and analysis of historical data. Before cloud computing security risk identification, the existing theoretical research and related materials on cloud computing security risk factors and security applications are collected, collated and analyzed.
II. Establishment of HHM framework of cloud computing security risk. A full understanding of cloud computing risks is acquired by means of expert research and academic seminars, and a preliminary HHM framework of cloud computing security risks is established. In this paper, according to the security architecture of cloud computing, cloud computing security risk factors are analyzed from three domains (1st hierarchy), which are cloud computing security operation management, cloud computing security technology implementation and cloud computing security support platform [8C.R. Chen, Y.T. Li, G.P. Liu, and L.W. Yang, Cloud Computing Services - Operations, Management, and Technical Architecture., China Tsinghua University Publishers: Beijing, 2014.] to establish the preliminary HHM framework.
III. Identification of cloud computing security risks. Based on the HHM framework, the three domains of cloud computing security risks are broken down again. The domain of cloud computing security operation management, for example, can be broken down into security operations, business continuity and backup and security operation organization process (2nd hierarchy). Security operations can be classified into four factors – monitoring and warning, security scan and penetration test, security audit and privacy protection (3rd hierarchy). At this point, these four specific factors cannot be broken down again, and therefore they are the atomic objects in the final analysis of cloud computing security system.
IV. Analysis of cloud computing security risks. Cloud computing security risk factors are analyzed based on HHM to identify potential security risks and risk factors and establish a formal cloud computing security risk factors HHM framework (Fig. 1), which lays the foundation for cloud computing security assessment.
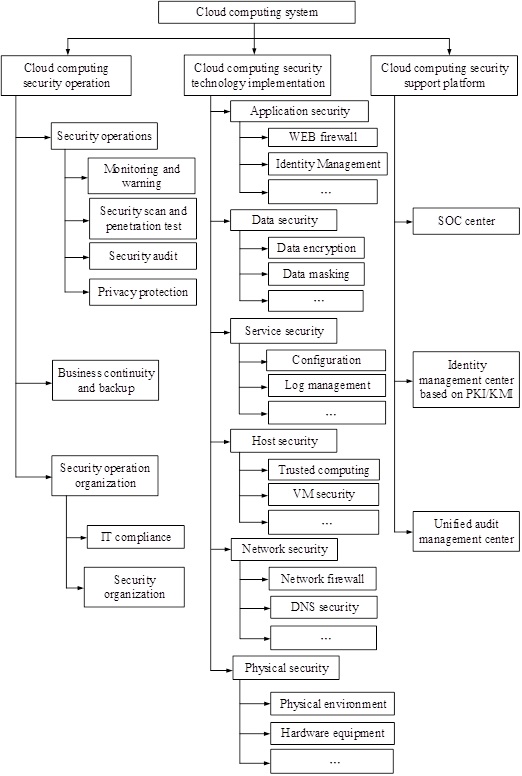 |
Fig. (1) Cloud computing security risk factors HHM framework. |
It should be noted that cloud computing security risk identification requires a cyclic iterative process (factor acquisition → cloud computing security HHM diagram → factor acquisition → …) to ultimately determine cloud computing security risk factors. If a certain cloud computing security risk source cannot be determined by using the current HHM framework, then the framework should be constantly improved and extended in new dimensions for the identification of all cloud computing security risk factors through the continuous cycle. According to “Security Guidance for Critical Areas of Focus in Cloud Computing V3.0” released by Cloud Security Alliance (CSA), cloud computing security operation management involves cloud computing architectural framework, governance and enterprise risk management, legal issues and electronic discovery, compliance and audit, information management and data security and other key domains; cloud computing security technology implementation includes traditional security, business continuity and disaster recovery, data center operations, incident response, application security, encryption and key management, identity, entitlement and access management, virtualization, etc.; cloud computing security operation management, technology implementation and support platform all demonstrate the critical domain of security as a service. As interoperability and portability (Domain 6) involves business compatibility and portability among multiple operators, it is not unique to cloud computing risk factors. Therefore by applying HHM to cloud computing security risk identification phase, risk factors can be fully captured and identified.
3.2. Cloud Computing Security Risk Calculation
Cloud computing security risks and the probability of potential security incidents along with the resulting losses are closely related. Therefore, the probability and losses must be quantified for relatively accurate measurement of cloud computing security risks. According to GB/T 20984-2007 (Risk Assessment Specification for Information Security), risk calculation of information systems follows the paradigm: risk value = R(A, T, V) (R represents a security risk calculation function; A stands for assets; T represents threats, V indicates vulnerability). The degree of the impact of risk on assets, threat frequency and vulnerability severity is defined as levels 1-5. Cloud computing is a “special” information system, and its security risk value R can be regarded as function of assets, threats and vulnerability. Namely, cloud computing security risk R = G (c, t, f), where c is impact on assets, t is threat frequency, f is vulnerability severity.
As shown in HHM framework, risk factors resulting in cloud computing security incidents have the characteristics of complexity, ambiguity and uncertainty. Therefore, fuzzy comprehensive evaluation method is chosen for the calculation of cloud computing security risks [9Y. Fu, X.P. Wu, Q. Ye, and X. Peng, "An approach for information systems security risk assessment on fuzzy set and entropy-weight", Tien Tzu Hsueh Pao, vol. 38, no. 7, pp. 1489-1494, 2010., 10R. Jiang, Z.F. Ma, T. Li, and Q.J. Zhang, "Study on security risk assessment for technology of cloud computing", App. Elec. Tech., vol. 41, no. 3, pp. 111-115, 2015.]. The evaluation of security risk factors and the construction of membership matrix of the corresponding evaluation set are completed with the use of fuzzy set theory from dimensions of impact on assets, threat frequency and vulnerability severity, and the entropy weight method is used to determine the weight of risk factors to the security risks of cloud computing. Ultimately the security risk values of the three dimensions are determined and quantified into cloud computing security risk values and their corresponding levels.
3.2.1. Fuzzy Sets and Membership Matrices
Firstly, a set of risk factors for cloud computing security is established. Let A={a1, a2,…, an}, where n is the number of risk factors.
Secondly, evaluation sets are constructed. Different evaluation sets Bc, Bt, Bf are set up for assets, threats and vulnerability respectively: Bc = {bc1, bc2, …, bci}, Bt = {bt1, bt2, …, btj}, Bf = {bf1, bf2, …, bfk}, where i, j and k represent the number of factors in corresponding evaluation sets.
Thirdly, fuzzy mapping is conducted. Different factors in risk factor set A are evaluated with the use of evaluation set B, and fuzzy mapping is f:A→F(B). F(B) is the fuzzy set of B, ai→f(ai) = {pi1, pi2,…,pim}
 F(B), where f represents the degree of support of risk factor ai for each index in evaluation sets.
F(B), where f represents the degree of support of risk factor ai for each index in evaluation sets.
Fourthly, membership matrices are constructed. The membership vector of risk factor ai for evaluation set B is pi = {pi1, pi2,…,pim} (i=1,2,…,n), where n is the number of risk factors and m is the number of indexes in corresponding evaluation sets. Cloud computing security risk membership matrix is:
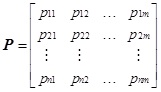 |
Similarly, membership matrices of impact on assets, threat frequency and vulnerability severity are Pc, Pt and Pf respectively.
3.2.2. Entropy Weight of Risk Factors
Firstly, assuming that the system may be in different states n: S1,S2,…,Sn, Pi represents the probability that the system is in state Si, where i=1,2,…,n, 0≤Pi≤1,
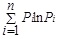 =1. Then the entropy can be expressed as:
=1. Then the entropy can be expressed as:
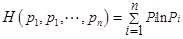 |
(1) |
The information entropy H indicates the orderly degree of the system.
Secondly, the relative importance of risk factor ai can be measured by entropy:
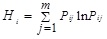 |
(2) |
Here pij (i=1,2,…,n;j=1,2,…,m) represents the degree of support of risk factors for each index in evaluation sets. The closer they are equal to each other, the greater the entropy value and uncertainty of risk factor ai to cloud computing security assessment is.
Thirdly, formula (2) is normalized by using Hmax (Hmax=lnm) for the entropy of relative importance which measures cloud computing security risk factor ai:
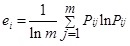 |
(3) |
According to the formula (2), when the values of pij are equal, ei is the maximum value 1, that is 0≤ ei ≤1. When the entropy of relative importance of risk factor ai is the maximum value, this risk factor’s contribution to cloud computing security risk assessment is the smallest.
Fourthly, normalization is conducted again by using 1-ei to represent the weight of cloud computing security risk factor ai, and the weight value is:
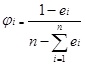 |
(4) |
3.2.3. Index Weight Vector of Each Evaluation Set
When calculating the impact on assets, the corresponding weight is given to each index in evaluation sets, and the index weight vector Ui= (u1,u2,…,ui). Similarly, the index weight vector of threat frequency evaluation set is Vj = (v1, v2,…,vj), and the index weight vector of vulnerability severity evaluation set is Wk = (w1, w2,…,wk).
3.2.4. Cloud Computing Security Risk Values
According to the formula (4), the corresponding weight vector of cloud computing security risk factors is φi=(φ1, φ2,…,φn), where i=1,2,…,n. The security risk value of impact on assets is:
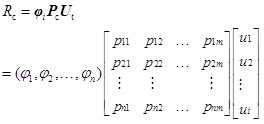 |
(5) |
Similarly, the security risk values of threat frequency and vulnerability severity are Rt and Rf. Cloud computing security risk value is:
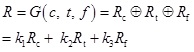 |
(6) |
Here k1, k2 and k3 represent the relative importance of the three aspects, and satisfy k1 + k2 + k3 = 1.
As shown in cloud computing security risk factors HHM framework, cloud computing system is composed of multiple security domains; a cloud security domain is composed of multiple security classes and a certain security class is composed of multiple risk factors. The overall risk level value of cloud computing is:
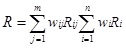 |
(7) |
Here wi stands for the weight of the i-th security class in a specific domain (i=1,2,…,n), and satisfies w1 + w2 + …+ wn = 1; Ri stands for the risk value of the n-th security class. wij represents the weight of the j-th security domain (j=1,2,…,m), and satisfies wi1+wi2+…+win=1; Rij represents the risk value of the j-th security domain.
3.2.5. Cloud Computing Security Risk Levels
When the security risk value of cloud computing system is determined, security risk level can be decided according to security risk membership levels (Table 1).
4. APPLICATION CASE
To verify the validity and correctness of the construction system and assessment method in this paper, a cloud computing platform of a school is used as an example for analysis. Security assessment is conducted in security domains of cloud computing security operation management, technology implementation and support platform.
4.1. Construction of Cloud Computing Risk Factors and Evaluation Sets
For simplicity, only the domain of “cloud computing security technology implementation” is used for analysis in this article. According to cloud computing security risk factors HHM framework (Fig. 1), security risk in this domain is subdivided and the risk factor set is as follows:
Given the parallel linear property of the secondary classification A1, A2,…, A6, here only application security (A1) is discussed, and the method can be applied to other classes. The security class A1 consists of six risk factors (Table 2), and its factor set is {a1, a2, a3, a4, a5, a6}. The assessment on impact on assets, threat frequency and vulnerability severity is categorized into five levels: high, relatively high, medium, relatively low, and low. Hence the evaluation set of A1 is Bc = {bc1, bc2,…,bc5}, Bt = {bt1, bt2,…,bt5}, Bf = {bf1, bf2,…,bf5}.
4.2. Membership Matrix
According to expert scoring method (15 experts), the degree of influence of risk factors on assets, threats and vulnerability are rated and the probability of each risk factor belonging to each evaluation index is calculated. The corresponding membership matrices Pc, Pt, and Pf are shown in Table 3.
4.3. The Weight Vector of Each Evaluation Index
θc = ( θc1, θc2, θc3, θc4, θc5, θc6) = (0.109, 0.313, 0.160, 0.109, 0.200, 0.109)
θt = ( θt1, θt2, θt3, θt4, θt5, θt6) = (0.105, 0.197, 0.017, 0.372, 0.112, 0.197)
θf = ( θf1, θf2, θf3, θf4, θf5, θf6) = (0.117, 0.101, 0.206, 0.252, 0.117, 0.206)
The corresponding weights of evaluation sets of assets, threats and vulnerability are:
U = (1/15, 5/15, 3/15, 2/15, 4/15)
V = (3/15, 2/15, 4/15, 1/15, 5/15)
W = (2/15, 3/15, 5/15, 1/15, 4/15)
4.4. Identification of Cloud Computing Security Risk Value and Risk Level
According to formulas (5) and (6), the risk values of cloud computing application security in three dimensions (A1) are:
Rc = θcPcUT = 0.186
Rt = θtPtVT = 0.202
Rf = θfPfWT = 0.184.
For cloud computing application security class (A1), assets, threats and vulnerability are of equal importance, therefore k1=k2=k3=1/3, and the risk value of this class (A1) is R1 = k1Rc + k2Rt + k3Rf = 0.191.
According to formula (7), the computing security risk value is:
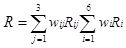 =0.173, where i=6, j=3.
=0.173, where i=6, j=3.
According to Table 1, the cloud computing platform security risk level of this school is low.
CONCLUSION
Cloud computing security risk assessment is a complex process. In this paper, hierarchical holographic modeling method is applied in cloud computing risk identification phase, which ensures a comprehensive, effective and clear capture of risk factors. Additionally, with the application of fuzzy set theory and entropy weight method, the interrelations among various risk factors are identified and the result of risk assessment is quantified for a comprehensive evaluation. The analysis of the example demonstrates that this method is simple and feasible and it provides an effective way for the study of cloud computing security risk assessment. However, the accuracy of input data acquired by expert scoring method and whether security domains, classes and their interrelations is a simple linear relationship require further exploration and research.
CONFLICT OF INTEREST
The authors confirm that this article content has no conflict of interest.
ACKNOWLEDGEMENTS
The authors would like to appreciate the support from Humanities and social science project of Hubei Provincial Department of Education (No. 15Q065).
REFERENCES
| [1] | K.L. Neela, V. Kavitha, and R.K. Ramesh, "Cloud computing: Threats and security issues", Int. J. Engi. Sci. Res. Tech., vol. 2, no. 8, pp. 2070-2072, 2013. |
| [2] | R. Latif, H. Abbas, S. Assar, and Q. Ali, "Cloud Computing Risk Assessment: A Systematic Literature Review", In: J.J. Park, I. Stojmenovic, M. Choi, and F. Xhafa, Eds., Future Information Technology, vol. 276. Germany Springer Publishers, Verlag: Berlin, 2014, pp. 285-295. |
| [3] | C.K. Fan, and T.C. Chen, "The risk management strategy of applying cloud computing", Int. J. Adv. Comp. Sci. App., vol. 3, no. 9, pp. 18-27, 2012. |
| [4] | C. Schllings, and S. Simom, "Risk Management on the Security Problem in Cloud Computing", In: First ACIS/JNU International Conference on Computer, Networks, System and Industrial Engineering, 2011, pp. 147-152. |
| [5] | H.B. Wang, F. Liu, and H. Liu, "A Method of the Cloud Computing Security Management Risk Assessment", In: D.H. Zeng, Ed., Advances in Intelligent and Soft Computing, vol. 141. Germany Springer Publishers, Verlag: Berlin, 2012, pp. 609-618. |
| [6] | S.H. Albakri, B. Shanmugam, G.N. Samy, N.B. Ldris, and A. Ahmed, "Security risk assessment framework for cloud computing environments", Security Com. Netw., vol. 7, no. 11, pp. 2114-2124, 2014. [http://dx.doi.org/10.1002/sec.923] |
| [7] | T.P. Chen, L.J. Zheng, and X.Y. Zhang, "Application of HHM in risk identification of information system", J. Safety Sci. Tech., vol. 4, no. 6, pp. 98-100, 2008. |
| [8] | C.R. Chen, Y.T. Li, G.P. Liu, and L.W. Yang, Cloud Computing Services - Operations, Management, and Technical Architecture., China Tsinghua University Publishers: Beijing, 2014. |
| [9] | Y. Fu, X.P. Wu, Q. Ye, and X. Peng, "An approach for information systems security risk assessment on fuzzy set and entropy-weight", Tien Tzu Hsueh Pao, vol. 38, no. 7, pp. 1489-1494, 2010. |
| [10] | R. Jiang, Z.F. Ma, T. Li, and Q.J. Zhang, "Study on security risk assessment for technology of cloud computing", App. Elec. Tech., vol. 41, no. 3, pp. 111-115, 2015. |