- Home
- About Journals
-
Information for Authors/ReviewersEditorial Policies
Publication Fee
Publication Cycle - Process Flowchart
Online Manuscript Submission and Tracking System
Publishing Ethics and Rectitude
Authorship
Author Benefits
Reviewer Guidelines
Guest Editor Guidelines
Peer Review Workflow
Quick Track Option
Copyediting Services
Bentham Open Membership
Bentham Open Advisory Board
Archiving Policies
Fabricating and Stating False Information
Post Publication Discussions and Corrections
Editorial Management
Advertise With Us
Funding Agencies
Rate List
Kudos
General FAQs
Special Fee Waivers and Discounts
- Contact
- Help
- About Us
- Search

The Open Electrical & Electronic Engineering Journal
(Discontinued)
ISSN: 1874-1290 ― Volume 13, 2019
Shape Adaptable Medical Multimedia Processing
Ali J. Abboud*
Abstract
Introduction:
Electronic medical healthcare systems are becoming the backbone of health organizations over the world. The huge amounts of medical multimedia produced by these systems especially images and videos are transmitted by the computer networks that connect these systems. The variability in the shape and texture of transferred medical multimedia data needs adaptable procedures to process these data efficiently. In other words, these procedures must adjust automatically based on the shape of region of interests in the medical multimedia images to cope with fast changes in the healthcare environments. In this paper, we have proposed shape adaptable watermarking approaches for medical multimedia processing systems. The medical images generated by X-rays, MRI and CT modalities are used in our experiments to test proposed approaches. In addition, these approaches were tested under different kinds of signal processing and geometric attacks. The comparative comparison of our proposed approaches with state-of-art approaches proved the superiority and capability of our approaches to adjust the number of selected subands of medical cover image to embed and extract the hospital watermark logos.
Background and Objective:
The development of an adjustable approach to process medical multimedia signals for healthcare system. The aim of this research is to select adaptably the number of subands of cover image to hide the information of hospital logo watermark inside them such that embedded watermarks can resist different kinds of attacks.
Method:
The proposed adjustable approach consists of suband selection method, criterion, embedding and extraction procedures, DWT transform, attacks, evaluation metrics, etc.
Results & Conclusion:
It provides robust and adjustable method to embed and extract watermark logo at different resolution levels of cover medical image and uses with images of different sizes and modalities.
Article Information
Identifiers and Pagination:
Year: 2019Volume: 13
First Page: 1
Last Page: 18
Publisher Id: TOEEJ-13-1
DOI: 10.2174/1874129001913010001
Article History:
Received Date: 9/12/2018Revision Received Date: 25/12/2018
Acceptance Date: 28/12/2018
Electronic publication date: 31/1/2019
Collection year: 2019
open-access license: This is an open access article distributed under the terms of the Creative Commons Attribution 4.0 International Public License (CC-BY 4.0), a copy of which is available at: (https://creativecommons.org/licenses/by/4.0/legalcode). This license permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
* Address correspondence to this author at the Department of Computer Engineering, College of Engineering, University of Diyala, Diyala Governorate, Iraq, E-mail: ali.j.abboud@gmail.com
| Open Peer Review Details | |||
|---|---|---|---|
| Manuscript submitted on 9-12-2018 |
Original Manuscript | Shape Adaptable Medical Multimedia Processing | |
1. INTRODUCTION
Medical healthcare is one of the most important sectors in the daily life activities of human beings. The traditional healthcare practices used paper based medical reports and diagnoses to help doctors and specialists to make suitable decisions to treat their patients [1A.K. Gupta, and M.S. Raval, "A robust and secure watermarking scheme based on singular values replacement", Sadhana, vol. 37, no. 4, pp. 425-440.
[http://dx.doi.org/10.1007/s12046-012-0089-x] ]. Nowadays, telemedicine revolutionize the traditional practices and procedures by exchanging medical images and patient’s records electronically across all world hospitals. Indeed, telemedicine is becoming the imperative tool in the infrastructure of all healthcare systems [2A. Zear, A.K. Singh, and P. Kumar, "A proposed secure multiple watermarking technique based on DWT, DCT and SVD for application in medicine", Multimedia Tools Appl., vol. 77, no. 4, pp. 4863-4882.
[http://dx.doi.org/10.1007/s11042-016-3862-8] ]. This tool uses modern computer technologies to provide electronic healthcare services to the people living in rural and far areas. Those people in the past, need to travel for long distances to obtain necessary diagnosis and treatment, however currently, telemedicine made this task very easy by contacting physicians and doctors remotely and giving right consultation to those patients [3A. Al-Haj, and A. Amer, "Secured telemedicine using region-based watermarking with tamper localization", J. Digit. Imaging, vol. 27, no. 6, pp. 737-750.
[http://dx.doi.org/10.1007/s10278-014-9709-9] [PMID: 24874408] ].
Hence, we can say that telemedicine is an effective apparatus to serve patients accurately and quickly. However, interchanging medical images and patient records electronically by this tool through the computer networks especially global internet makes these sensitive data vulnerable to different kinds of intentional attacks. These attacks can modify, insert or delete the contents of medical data [4A. Al-Haj, G. Abandah, and N. Hussien, "Crypto-based algorithms for secured medical image transmission", IET Inf. Secur., vol. 9, no. 6, pp. 365-373.
[http://dx.doi.org/10.1049/iet-ifs.2014.0245] ]. In addition, the accidental attacks such as noise, compression, rotation and scaling translation have adverse effects on the performance of medical healthcare systems. To make the electronic health system robust to all these attacks, there are certain information security approaches to deal effectively with all these attacks. These security services should be available in all healthcare systems to protect information of patients and medical staff. Confidentiality, authentication and integrity are the main security characteristics that should be available in any telemedicine system in order to be secure enough to provide medical services robustly. Confidentiality guarantees that only intended parties will use medical multimedia information while authentication assures that the medical multimedia information comes from authorized source. On the other hand, the integrity service find out whether the medical data modified or not through transmission from source to destination [5R. Eswaraiah, and E.S. Reddy, "Robust medical image watermarking technique for accurate detection of tampers inside region of interest and recovering original region of interest", IET Image Process., vol. 9, no. 8, pp. 615-625.
[http://dx.doi.org/10.1049/iet-ipr.2014.0986] , 6A.J. Abboud, A.N. Albu-Rghaif, and A.K. Jassim, "Balancing compression and encryption of satellite imagery", Iran. J. Electr. Comput. Eng., vol. 8, no. 5, pp. 3568-3586.].
Cryptography, digital signatures, hashes and watermarking hiding algorithms are used to satisfy earlier explained information security characteristics in the healthcare systems. Cryptography is one of strongest tools to provide confidentiality for different kinds of multimedia data including text, images, voice and videos while digital signatures and hashes are used extensively to check the integrity of multimedia files. In addition, watermarking algorithms are used to provide authentication and copyright of data and recently used to recover tampered areas of multimedia file .The rest of paper is organized as follows: Section 2 is devoted to explain background material and Section 3 is used to present developed method. In addition, Section 4 is used to explain our experimental results. Finally, conclusion is presented in Section 5.
2. BACKGROUND
Medical multimedia processing refers to the creating and manipulating the visual information of medical data to diagnosis and treat patients accurately. These medical multimedia include image, voice or/and video signal of the diagnosed organs inside the body of the patient. The shape of patient’s organs may be changed according to the health status of the sick person. Sometimes, the organ is healthy and has normal shape while in other states, the size and shape of this organ is changed significantly for its sickness by infections, microbes, germs or bacteria. Hence, we can conclude that the size and shape of organs will change according to the condition of the patient. For earlier reasons, this research is aimed at developing dynamic algorithms that can adapt to the shape, size and health of patient organs. These developed algorithms process medical images dynamically. We have to mention that medical multimedia images may have one or more regions of specific importance to the doctor. These regions are called Regions Of Interest (ROI) and irrelevant regions for medical staff and doctors are called Regions Of No Interest (RONI). The details of the ROI are very important for diagnosing and treating the people, hence, this region should be protected from any intentional or accidental changes such as tampering, rotation, shear, translation, scaling, compression or tampering. Several algorithms were used in this research study as described below.
2.1. Discrete Wavelet Transform
Many approaches have been proposed in the literature to analyse and extract useful information from digital signals and images either in the spatial or transform domain [7H. Al-Assam, A.J. Abboud, and S.A. Jassim, "Hidden assumption of face recognition evaluation under different quality conditions"", IEEE International Conference on Information Society (i-Society), England., ., 8S. Bravo-Solorio, F. Calderon, C-T. Li, and A.K. Nandi, "Fast fragile watermark embedding and iterative mechanism with high self-restoration performance", Digital Signal Processing, vol. 73, pp. 83-92.
[http://dx.doi.org/10.1016/j.dsp.2017.11.005] , 9P. Dong, J.G. Brankov, N.P. Galatsanos, Y. Yang, and F. Davoine, "Digital watermarking robust to geometric distortions", IEEE Trans. Image Process., vol. 14, no. 12, pp. 2140-2150.
[http://dx.doi.org/10.1109/TIP.2005.857263] [PMID: 16370466] ]. However, transform domain based approaches look more robust to any geometric modifications and attacks on the medical images [10A. Al-Haj, "Combined DWT-DCT digital image watermarking", J. Comput. Sci., vol. 3, no. 9, pp. 740-746.
[http://dx.doi.org/10.3844/jcssp.2007.740.746] ]. Such of these popular transforms are discrete wavelet transform (DWT), Discrete Cosine Transform (DCT), and Discrete Fourier Transform (DFT) [11A.J. Abboud, and S.A. Jassim, "Incremental fusion of partial biometric information", Mobile Multimedia/Image Processing, Security, and Applications 2012 by International Society for Optics and Photonics, vol. Vol. 8406, .
[http://dx.doi.org/10.1117/12.918776] , 12A.J. Abboud, and S.A. Jassim, "Image quality guided approach for adaptive modelling of biometric intra-class variations", 2010 Proceedings of SPIE - The International Society for Optical Engineering, .
[http://dx.doi.org/10.1117/12.850592] ]. Wavelet transform is the set of basis functions copied from base mother wavelet and they are orthogonal to each other. It characterizes by decomposing the image into several successive levels depending on the decomposition level and the size of the image. In this research, DWT is used in our research as image transform tool with aim to obtain information about medical image simultaneously in the spatial and frequency domains as in Fig. (1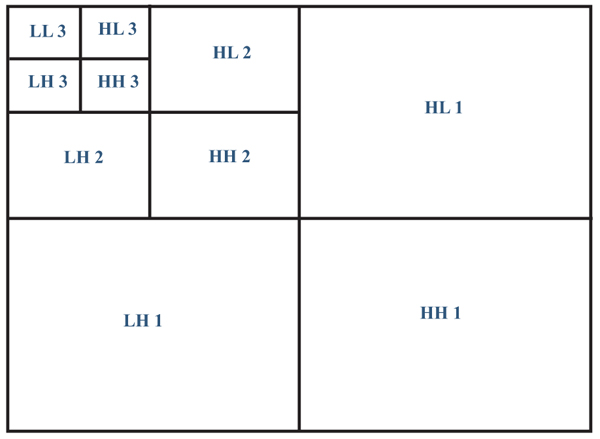 ).
).
 |
Fig. (1) Discrete wavelet transform decomposition of medical multimedia images. |
2.2. Watermarking Algorithms
Image watermarking is the state of art technology to provide several security services simultaneously. These services are the source authentication, patient identity checking and digital multimedia integrity verification [13A. Kahate, Cryptography and network security., McGraw-Hill Education, .]. These services are satisfied by embedding robust, semi fragile and fragile watermarks in the medical multimedia images. These watermarks may be visible or invisible in the multimedia signal depending on the application. Furthermore, these watermarks signals may be hidden in the spatial or/and transform domain(s) of the multimedia signal. For medical multimedia images of the patients, the watermarking algorithm should be reversible (i.e. we can recover watermarks without causing any distortion to the medical image). In addition, the watermarking algorithms should embed watermarks such that be robust to different kinds of intentional or accidental attacks.
2.3. Singular Value Decomposition
Singular Value Decomposition (SVD) is the mathematical tool to factorize matrix W into three matrices X, Y and Z [14A.N. Albu-Rghaif, A.K. Jassim, and A.J. Abboud, "A data structure encryption algorithm based on circular queue to enhance data security", Engineering Sciences-3rd Scientific Conference of Engineering Science (ISCES), 2018 1st International Scientific Conference of. IEEE, Baqubah, .
[http://dx.doi.org/10.1109/ISCES.2018.8340522] ]. If a matrix W of dimensions m x m, therefore the SVD of matrix W is:
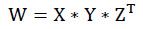 |
(1) |
Where X and Y are left and right orthonormal vectors and Y is the diagonal matrix of singular values. The singular values of Y are arranged in the diagonal in the descending order. The SVD is used in the signal and image processing for several reasons, which are [1A.K. Gupta, and M.S. Raval, "A robust and secure watermarking scheme based on singular values replacement", Sadhana, vol. 37, no. 4, pp. 425-440.
[http://dx.doi.org/10.1007/s12046-012-0089-x] ]: (1) there is a need to use less singular values to reproduce big part of signal power (2) we can use SVD with different sizes matrices (3) SVD singular values have good robustness to the attacks on the signal and multimedia images.
2.4. Performance Measures
The performance measurement of the biomedical multimedia processing system is evaluated using three main measures described below as follows:
2.4.1. Peak-To-Signal-Noise-Ratio (Psnr) Measure
PSNR is the most used measure to quantify the quality of multimedia signals including image, voice and video. This measure is comparing the peak power between original and corrupted signals as shown below:
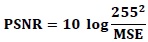 |
(2) |
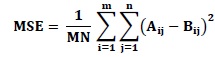 |
(3) |
Where MSE is the mean square error between the original image (A) and noisy image (B).
2.4.2. Structural Similarity Index (SSIM)
SSIM is a novel measure to quantify the degree of similarity between referenced and corrupted signals. The concept of measurement for this metric is based on the structure human vision system [15Z. Wang, A.C. Bovik, H.R. Sheikh, and E.P. Simoncelli, "Image quality assessment: from error visibility to structural similarity", IEEE Trans. Image Process., vol. 13, no. 4, pp. 600-612.
[http://dx.doi.org/10.1109/TIP.2003.819861] [PMID: 15376593] ]. It measures the structure, luminance and contrast using following equation:
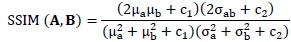 |
(4) |
The kernel sizes for images A and B are the variables a and b.
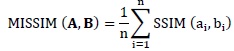 |
(5) |
MISSIM represents the mean SSIM over number of kernels referred to by variable n.
2.4.3. Normalized Cross Correlation Coefficient (Nc)
The normalized cross correlation coefficient (NC) measures the similarity between original and referenced images such that the higher value for this measure is one. It can be calculated as follows:
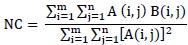 |
(6) |
Where A and B matrices represent the original and referenced signals (or images).
3. PROPOSED METHOD
We have proposed in this paper an adjustable (i.e. adaptable) method to embed watermarks in the frequency domain of transformed medical image. The adaptability is achieved by dynamically select one or more wavelet decomposition levels of medical cover image. The selection of type and level of wavelet decomposition is depending on the size and shape of medical image region. The procedures of embedding and extracting the secure watermarks are as follow:
3.1. Shape Adaptable Watermark Embedding Procedure
The procedure to embed watermarks in the medical multimedia image as follows:
- Start
- Segment the original multimedia medical image I into the ROI and RONI regions.
- Determine the size and shape (S) of ROI in the medical image.
- Based on the output (S) of step 3 specify the number (N: 1, 2, 3,4,5,6 or 7) and type (T: LL, LH, HL or HH) of decomposition levels of wavelet transform for medical cover image I. We will refer to the number of subands for embedding hospital watermark logo by (NS).
- Apply wavelet transform of kind (Haar) on the cover medical image I using (T and N) from step 4.
- Apply SVD on the selected subands (NS) of medical image I as follows:
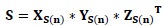
(7) - Compute SVD for the watermark logo W:
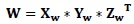
(8) - Replace the diagonal singular values (YS(n)) of selected subands of medical image I by the diagonal singular values (Yw) of W image.
- Do inverse SVD to obtain changed selected subands (NSw):
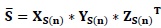
(9) - Do inverse DWT on the changed selected subands to obtain final watermarked cover image Iw.
- End
3.2. Shape Adaptable Watermarking Extracting Procedure
The procedure to extract watermarks from the medical multimedia image as follows:
- Start
- Segment the watermarked medical cover image Iw into the ROI and RONI regions.
- Determine the size and shape (S) of ROI in the medical image.
- Based on the output (S) of step 3, specify the number (N: 1, 2, 3,4,5,6 or 7) and type (T: LL, LH, HL or HH) of decomposition levels of wavelet transform for watermarked medical cover image Iw. We will refer to the number of subands for embedding hospital watermark logo by (NS).
- Apply wavelet transform of kind (Haar) on the watermarked cover medical image Iw using (T and N) from step 4.
- Apply SVD on the selected subands (NS) of medical image Iw as follow:
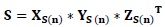
(10) - Extract the embedded singular values in the selected subands of cover image (YS(n)).
- Compute SVD for the watermark logo W:
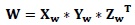
(11) - Re building watermarks using the extracted singular values in step 7 and the left and right orthonormal vectors of matrix W of step 8.
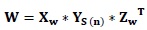
(12) - End
4. EXPERIMENTAL RESULTS AND DISCUSSION
We have conducted experiments to testify the possibility of our proposed method to adjust the location of hiding watermarks according to the shape of ROI in the medical image. The proposed method was tested in these experiments using images of CT and MRI and X-ray medical modalities. Also, these experiments were performed in three groups according to the type of wavelet decomposition level (LH, HL and HH). Several kinds of attacks have been applied to the watermarked medical image to test the robustness of the proposed method to resist such kind of attacks. We have chosen mean, median, noise, rotate, shear, compression and tampering as the potential attacks on the shape adjustable medical processing system. Figs. (2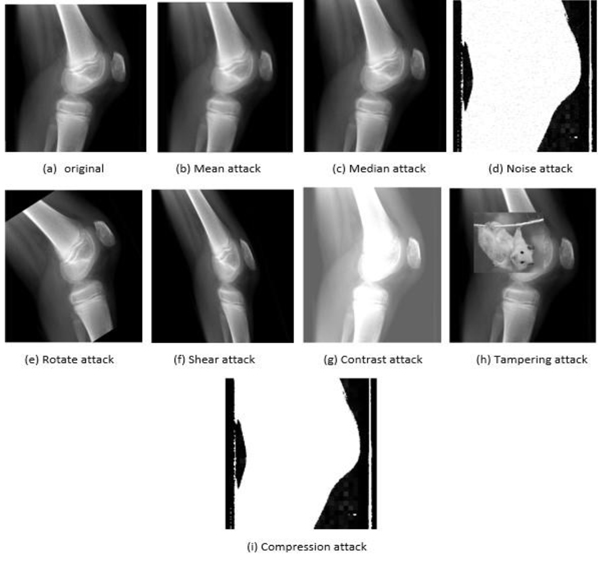 , 3
, 3 and 4
and 4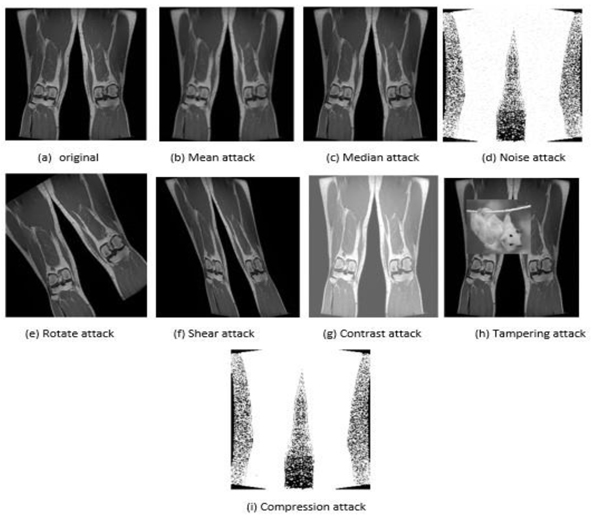 ) presented to show examples of these attacks on the images of three different imaging modalities.
) presented to show examples of these attacks on the images of three different imaging modalities.
 |
Fig. (2) An example of attacks on the X-rays modality of knee medical image. |
 |
Fig. (3) An example of attacks on the CT scan modality of brain medical image. |
4.1. LH Decomposition Level Experiments
LH subband is used in this group of experiments to hide the hospital watermark logo. The medical image is decomposed from level one until level seven (1-7). It means that there are seven decomposition levels for each tested medical image. Where LHn (i.e. LH1, i.e. LH2, i.e. LH3, i.e. LH4, LH5, LH6, LH7) on the horizontal axis in the Fig. (5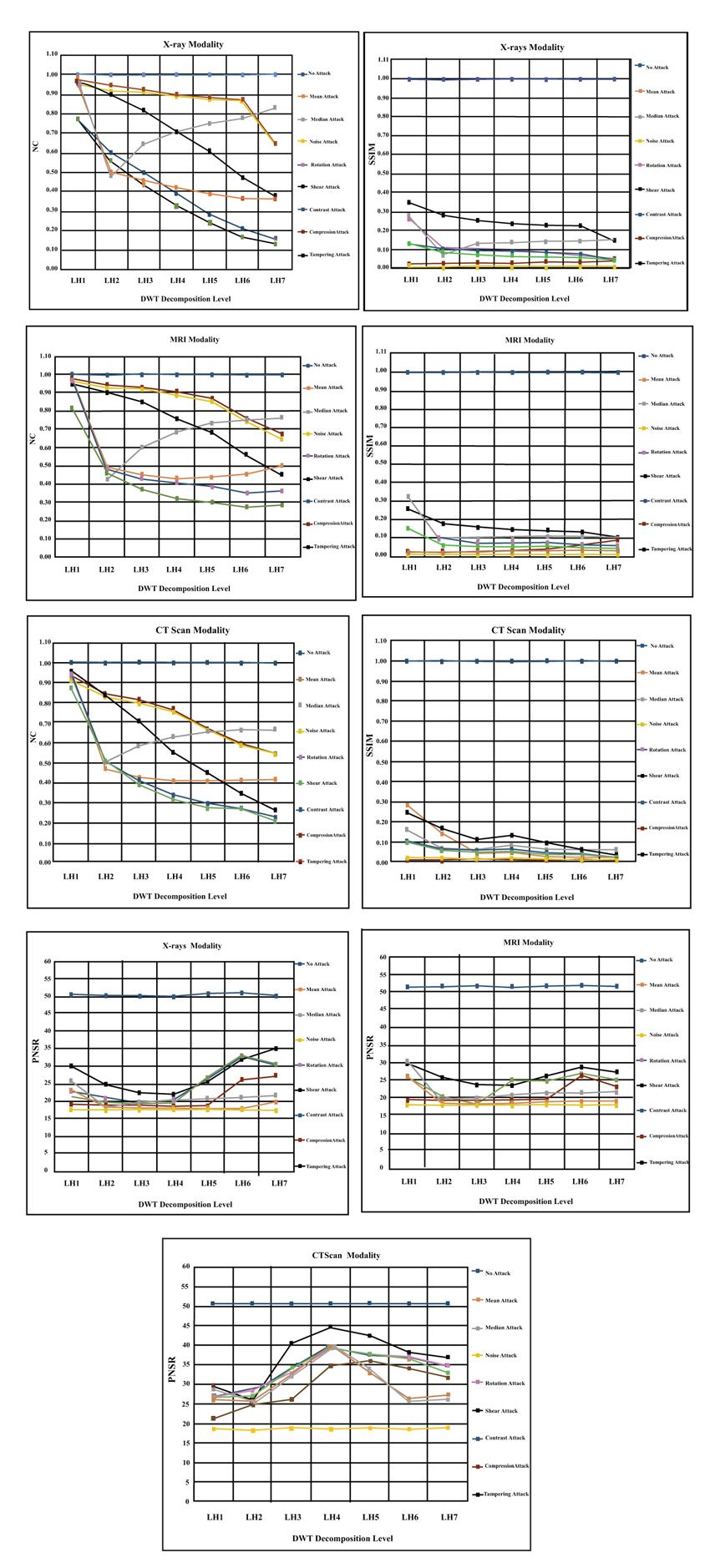 ) below refers to the groups of LH subands and does not mean the LH level number as conventionally known. For example, LH3 is the group of three LH subands {LHlevel 1 + LHlevel 2 + LHlevel 3}. We have noticed from the experimental results presented in the Fig. (5
) below refers to the groups of LH subands and does not mean the LH level number as conventionally known. For example, LH3 is the group of three LH subands {LHlevel 1 + LHlevel 2 + LHlevel 3}. We have noticed from the experimental results presented in the Fig. (5 ), that all the applied attacks have worse effect on the watermark logo image. However, only the contrast attack has less or no influence on the reconstructed watermark and has the same metrics values similar to the case of no attack on the medical image. For the rest of the attacks, we can say that the noise is the most powerful attack on the watermarked medical image. The big impact of this attack is apparent in the experimental results by making SSIM measure value (< 0.1) and NC measure value (< 0.6) and the PSNR measure value (< 20 dB). In addition, we have noticed that the noise attack effect becomes worse when goes deeper in the decomposition levels. Mean and median are the next influential attacks that have apparent effect on the reconstructed watermark logo. We can observe from the presented results below that these attacks made the SSIM metric value (0.2) and NC metric value (<0.5) and PSNR metric value (< 30 dB). However, we have noticed that the mean attack has consistent worse effect among all decomposition levels while the median attack starts to have less influence on the performance of the system from level (LH3) onwards. The rotate and shear geometric attacks are the next group in this sequence of attacks. The deteriorated effect of geometric attacks begins to appear from third decomposition level onwards, hence, we advise to use third level to embed watermark logos. Now, let analyze the influence of the last two attacks (i.e. tampering and compression). The tampering attack has less influence on the performance of the system than compression attack as proved in the terms of SSIM and PSNR metrics values in the Fig. (5
), that all the applied attacks have worse effect on the watermark logo image. However, only the contrast attack has less or no influence on the reconstructed watermark and has the same metrics values similar to the case of no attack on the medical image. For the rest of the attacks, we can say that the noise is the most powerful attack on the watermarked medical image. The big impact of this attack is apparent in the experimental results by making SSIM measure value (< 0.1) and NC measure value (< 0.6) and the PSNR measure value (< 20 dB). In addition, we have noticed that the noise attack effect becomes worse when goes deeper in the decomposition levels. Mean and median are the next influential attacks that have apparent effect on the reconstructed watermark logo. We can observe from the presented results below that these attacks made the SSIM metric value (0.2) and NC metric value (<0.5) and PSNR metric value (< 30 dB). However, we have noticed that the mean attack has consistent worse effect among all decomposition levels while the median attack starts to have less influence on the performance of the system from level (LH3) onwards. The rotate and shear geometric attacks are the next group in this sequence of attacks. The deteriorated effect of geometric attacks begins to appear from third decomposition level onwards, hence, we advise to use third level to embed watermark logos. Now, let analyze the influence of the last two attacks (i.e. tampering and compression). The tampering attack has less influence on the performance of the system than compression attack as proved in the terms of SSIM and PSNR metrics values in the Fig. (5 ). However, the bad effect of those two attacks generally increases gradually from the lowest decomposition band to the highest decomposition subband as shown in the Fig. (5
). However, the bad effect of those two attacks generally increases gradually from the lowest decomposition band to the highest decomposition subband as shown in the Fig. (5 ). To sum up, the worst attack on LH subband across all levels is the noise attack and the least effect (or no effect) attack on the shape adjustable system in this subband is the contrast attack.
). To sum up, the worst attack on LH subband across all levels is the noise attack and the least effect (or no effect) attack on the shape adjustable system in this subband is the contrast attack.
 |
Fig. (4) An example of attacks on the MRI modality of legs medical image. |
4.2. HL Decomposition Level Experiments
HL subband is used in this group of experiments to embed the hospital watermark logo. The medical image is decomposed into seven levels to embed watermark inside them. Where HLn (i.e. HL1, HL2, HL3, HL4, HL5, HL6, HL7) on the horizontal axis in the Fig. (6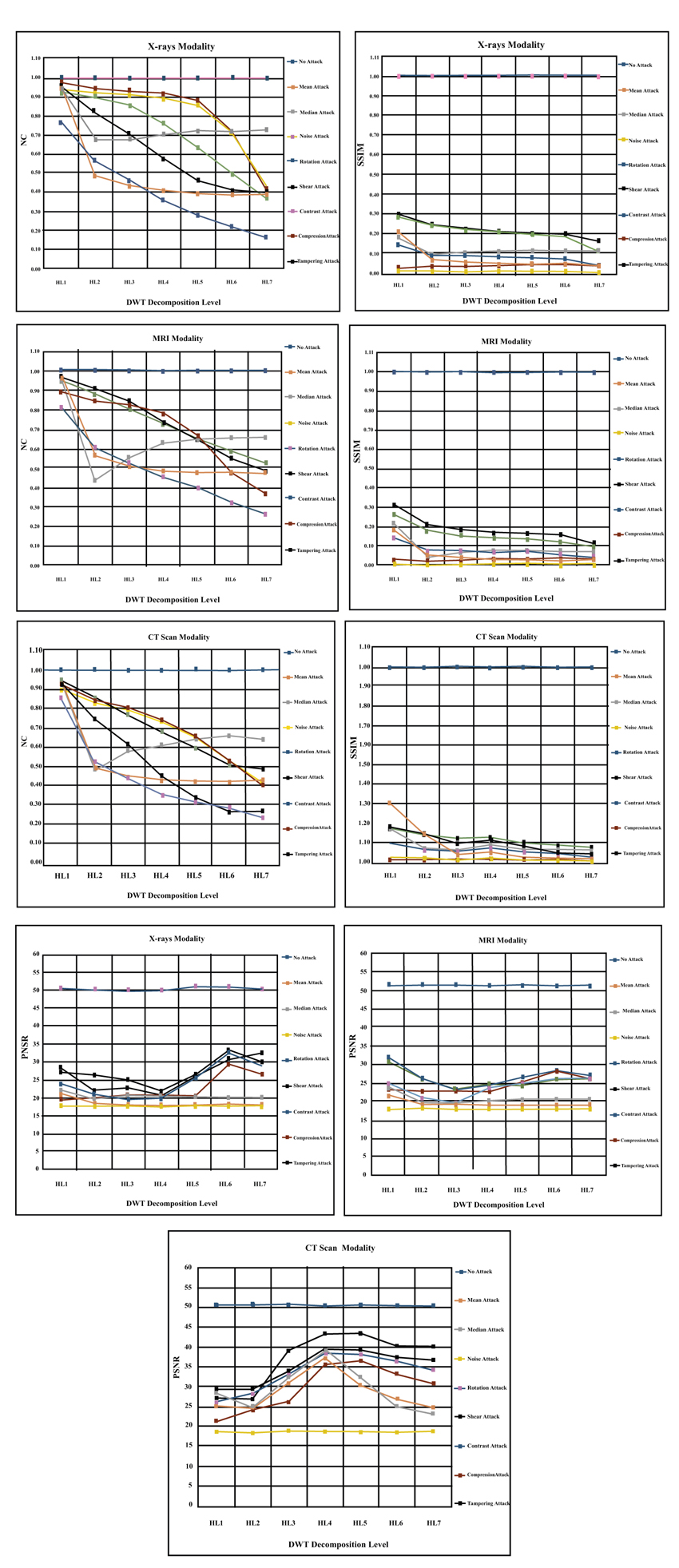 ) below refers to the groups of HL subands and does not mean the HL level number as conventionally known. For example, HL3 is the group of three HL subands {HLlevel 1 + HLlevel 2 + HLlevel 3}. We have noticed from the experimental results presented in the Fig. (6
) below refers to the groups of HL subands and does not mean the HL level number as conventionally known. For example, HL3 is the group of three HL subands {HLlevel 1 + HLlevel 2 + HLlevel 3}. We have noticed from the experimental results presented in the Fig. (6 ), that the all applied attacks have worse effect on the watermark logo image. This result add another evidence that the attacks have adverse effects on the performance of healthcare systems. However, only contrast attack has less or no influence on the reconstructed watermark and does not affect on medical processing system (i.e. similar to the case of no attack). For the remaining attacks, we can say that the noise is the most powerful attack on the watermarked medical image. The big impact of this attack is apparent in the experimental results by making SSIM measure value (< 0.1) and NC measure value (< 0.5) and the PSNR measure value (< 20 dB). In addition, we have noticed the same observation that the effect of noise attack becomes worst when goes deeper in the decomposition levels. Mean and median are the next influential attacks that have apparent effect on the reconstructed watermark logo. We can observe from the presented results below that these attacks made the SSIM metric value (0.2) and NC metric value (<0.5) and PSNR metric value (< 20 dB). However, we have noticed that the mean attack has consistent worse effect among all decomposition levels while the median attack starts to be less influence on the performance of the system from level (LH3) onwards. Hence, we advise to embed the watermarks from level three onwards. The rotate and shear geometric attacks are the next group in this sequence of attacks. The deteriorated effect of geometric attacks begins to appear from third decomposition level onwards, hence, we advise to use third level to embed watermark logos. Now, let analyze the influence of the last two attacks (i.e. tampering and compression). The tampering attack has less influence on the performance of the system than compression attack as proved in the terms of SSIM and PSNR metrics values in the (Fig. 6
), that the all applied attacks have worse effect on the watermark logo image. This result add another evidence that the attacks have adverse effects on the performance of healthcare systems. However, only contrast attack has less or no influence on the reconstructed watermark and does not affect on medical processing system (i.e. similar to the case of no attack). For the remaining attacks, we can say that the noise is the most powerful attack on the watermarked medical image. The big impact of this attack is apparent in the experimental results by making SSIM measure value (< 0.1) and NC measure value (< 0.5) and the PSNR measure value (< 20 dB). In addition, we have noticed the same observation that the effect of noise attack becomes worst when goes deeper in the decomposition levels. Mean and median are the next influential attacks that have apparent effect on the reconstructed watermark logo. We can observe from the presented results below that these attacks made the SSIM metric value (0.2) and NC metric value (<0.5) and PSNR metric value (< 20 dB). However, we have noticed that the mean attack has consistent worse effect among all decomposition levels while the median attack starts to be less influence on the performance of the system from level (LH3) onwards. Hence, we advise to embed the watermarks from level three onwards. The rotate and shear geometric attacks are the next group in this sequence of attacks. The deteriorated effect of geometric attacks begins to appear from third decomposition level onwards, hence, we advise to use third level to embed watermark logos. Now, let analyze the influence of the last two attacks (i.e. tampering and compression). The tampering attack has less influence on the performance of the system than compression attack as proved in the terms of SSIM and PSNR metrics values in the (Fig. 6 ). In general, the bad effect of those two attacks increases gradually from the lowest decomposition band to the highest decomposition subband as shown in the (Fig. 6
). In general, the bad effect of those two attacks increases gradually from the lowest decomposition band to the highest decomposition subband as shown in the (Fig. 6 ). Overall, the worst attack on HL subband across all levels is the noise attack and the least effect (or no effect) attack on the shape adjustable system in this subband is the contrast attack. Finally, we have noticed that the HL3, HL4 and HL5 are the best levels to embed watermark logos in the CT scan modality.
). Overall, the worst attack on HL subband across all levels is the noise attack and the least effect (or no effect) attack on the shape adjustable system in this subband is the contrast attack. Finally, we have noticed that the HL3, HL4 and HL5 are the best levels to embed watermark logos in the CT scan modality.
 |
Fig. (5) The results of embedding hospital logo across seven level in the LH Subband for X-rays, MRI and CT scan modalities. |
4.3. HH Decomposition Level Experiments
HH subband is used in this group of experiments to hide the hospital watermark logo. The medical image is decomposed into seven levels to embed watermark inside them. Where HHn (i.e. HH1, HH2, HH3, HH4, HH5, HH6, HH7) on the horizontal axis in the Fig. (7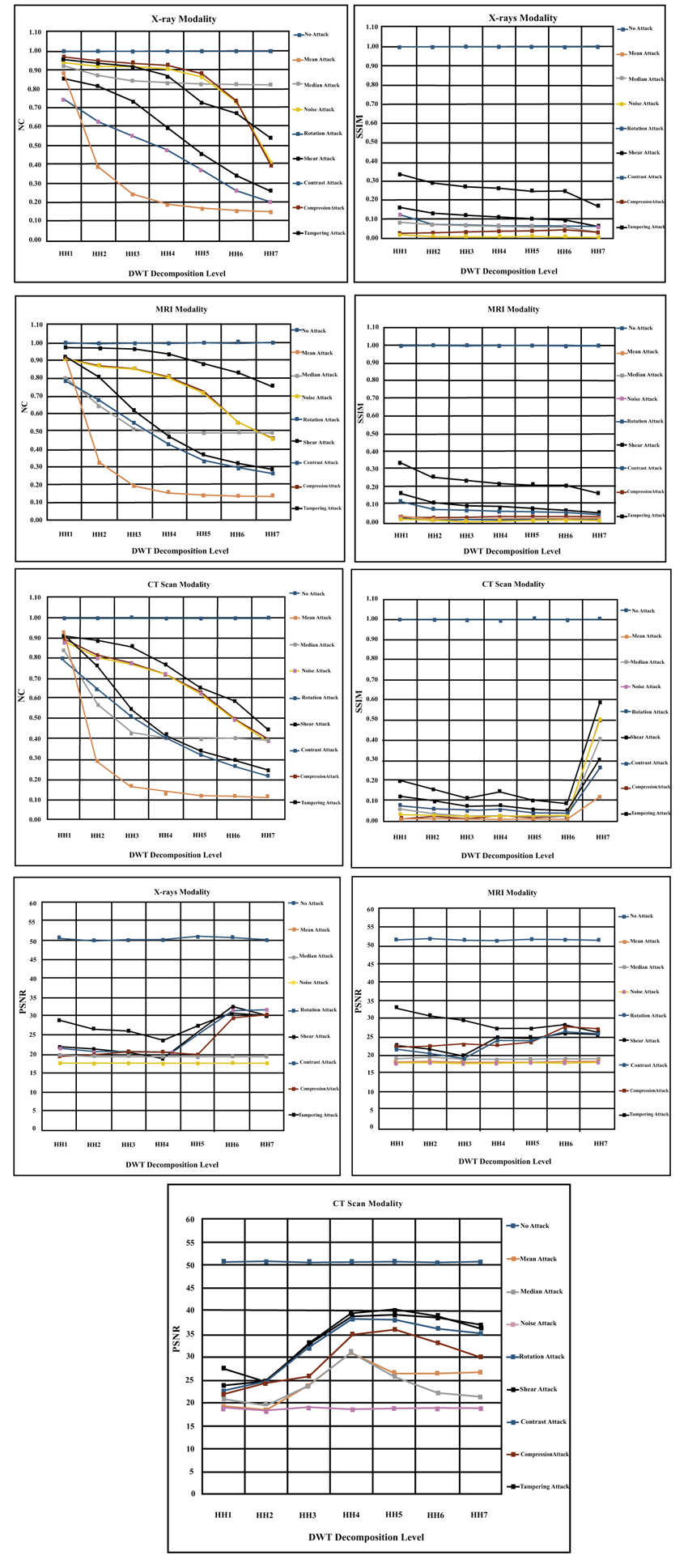 ) below refers to the groups of HH subands and does not mean the HH level number as conventionally known. For example, HH3 is the group of three HH subands {HHlevel 1 + HHlevel 2 + HHlevel 3}. We have noticed from the experimental results presented in the Fig. (7
) below refers to the groups of HH subands and does not mean the HH level number as conventionally known. For example, HH3 is the group of three HH subands {HHlevel 1 + HHlevel 2 + HHlevel 3}. We have noticed from the experimental results presented in the Fig. (7 ), that the all applied attacks have worse effect on the watermark logo image. These results add another evidence that the attacks have adverse effects on the performance of healthcare systems. However, only contrast attack has no influence on the reconstructed watermark and does not disturb medical processing system (i.e. similar to the case of no attack). For the remaining attacks, we can say that the noise is the most powerful attack on the watermarked medical image. The big impact of this attack is apparent in the experimental results by making SSIM measure value (< 0.1) and NC measure value (< 0.2) and the PSNR measure value (< 20 dB). We have also noticed that the effect of noise attack is consistent among all the HH decomposition levels of medical image. In addition, we have observed interesting result that the noise influence becomes the least in the seventh decomposition level in contrast to the presented results in the earlier two subsections. Mean and median are the next influential attacks that have apparent effect on the reconstructed watermark logo. We can observe from the presented results below that these attacks made the SSIM metric value (0.1) and NC metric value (<0.2) and PSNR metric value (< 20 dB). However, we have noticed that the mean attack has consistent worse effect among all decomposition levels while the median attack starts to be less influence on the performance of the system from level (HH3) onwards. Hence, we advise to embed the watermarks from level three onwards especially in level (HH4). The rotate and shear geometric attacks are the next group in this sequence of attacks. The deteriorated effect of geometric attacks begins to appear from third decomposition level onwards, hence, we advise to use third level to embed watermark logos. Now, let analyze the influence of the last two attacks (i.e. tampering and compression). The tampering attack has less influence on the performance of the system than compression attack as proved in the terms of SSIM and PSNR metrics values in the (Fig. 7
), that the all applied attacks have worse effect on the watermark logo image. These results add another evidence that the attacks have adverse effects on the performance of healthcare systems. However, only contrast attack has no influence on the reconstructed watermark and does not disturb medical processing system (i.e. similar to the case of no attack). For the remaining attacks, we can say that the noise is the most powerful attack on the watermarked medical image. The big impact of this attack is apparent in the experimental results by making SSIM measure value (< 0.1) and NC measure value (< 0.2) and the PSNR measure value (< 20 dB). We have also noticed that the effect of noise attack is consistent among all the HH decomposition levels of medical image. In addition, we have observed interesting result that the noise influence becomes the least in the seventh decomposition level in contrast to the presented results in the earlier two subsections. Mean and median are the next influential attacks that have apparent effect on the reconstructed watermark logo. We can observe from the presented results below that these attacks made the SSIM metric value (0.1) and NC metric value (<0.2) and PSNR metric value (< 20 dB). However, we have noticed that the mean attack has consistent worse effect among all decomposition levels while the median attack starts to be less influence on the performance of the system from level (HH3) onwards. Hence, we advise to embed the watermarks from level three onwards especially in level (HH4). The rotate and shear geometric attacks are the next group in this sequence of attacks. The deteriorated effect of geometric attacks begins to appear from third decomposition level onwards, hence, we advise to use third level to embed watermark logos. Now, let analyze the influence of the last two attacks (i.e. tampering and compression). The tampering attack has less influence on the performance of the system than compression attack as proved in the terms of SSIM and PSNR metrics values in the (Fig. 7 ). In general, the bad effect of those two attacks increases gradually from the lowest decomposition band to the highest decomposition subband as shown in the (Fig. 7
). In general, the bad effect of those two attacks increases gradually from the lowest decomposition band to the highest decomposition subband as shown in the (Fig. 7 ). Overall, the worst attack on HH subband across all levels is the noise attack and the least effect (or no effect) attack on the shape adjustable system in this subband is the contrast attack. Finally, we have noticed that the HH4, HL5 and HL6 are the best levels to embed watermark logos for all modalities.
). Overall, the worst attack on HH subband across all levels is the noise attack and the least effect (or no effect) attack on the shape adjustable system in this subband is the contrast attack. Finally, we have noticed that the HH4, HL5 and HL6 are the best levels to embed watermark logos for all modalities.
4.4. Medical Cover Image Experiments
In this subsection, we presented the experimental results of analyzing the effects of attacks on the medical cover image for X-rays, MRI and CT scan modalities as shown below in the Tables 1, 2 and 3. We have observed from these results that the X-rays modality images have higher metrics values than other two modalities. The median attack has higher metric values than other attacks on the medical image for all modalities. Compression and noise attacks have the least values for PSNR, SSIM and NC metrics among all presented attacks. In addition, the HH subband has the higher metric values among tested decomposition subands. These experimental results are consistent with the earlier presented results of embedded and extracted watermarks in the previous subsections.
Tables 4, 5, 6 and 7 are presented to show the number of coefficients of watermark image that can be embedded in the pixels of the cover image. In these tables, the following terms mean that the coefficients of one suband (1 Sub.), two subands (2 Sub.), three subands (3 Sub.) or four subands (4 Sub.) are used to embed the coefficient of watermark logo. Hence, if the size of image and the number of subands increased then we can hide more coefficients in the image. Figs. (8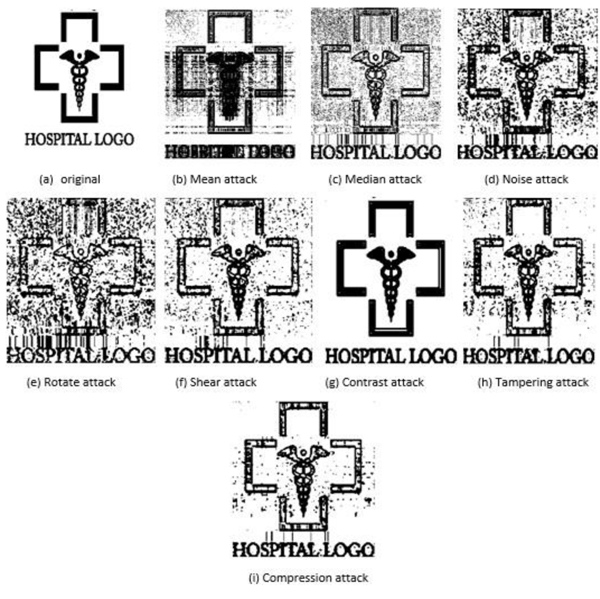 and 9
and 9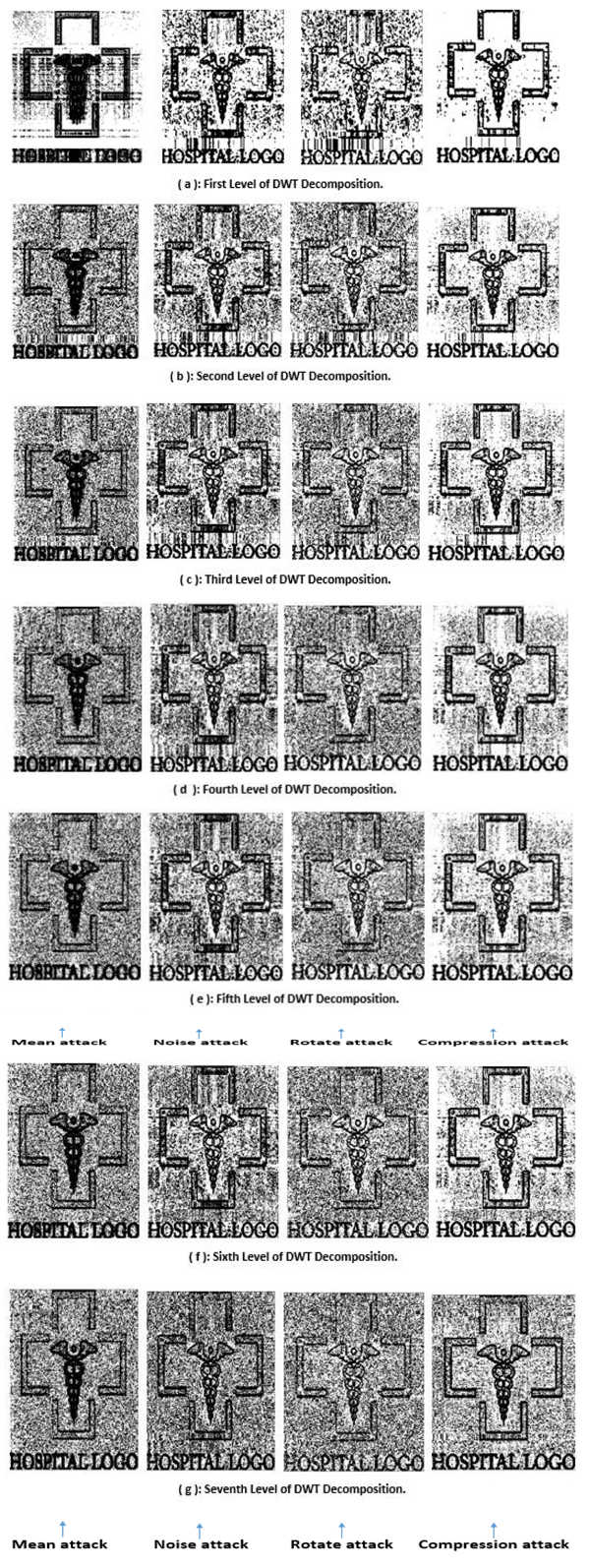 ) are presented to show an example of reconstructed watermark logos after disturbing the cover image by a number of different attacks that are described earlier.
) are presented to show an example of reconstructed watermark logos after disturbing the cover image by a number of different attacks that are described earlier.
 |
Fig. (6) The results of embedding hospital logo across seven levels in the HL Subband for X-rays, MRI and CT scan modalities. |
 |
Fig. (7) The results of embedding hospital logo across seven level in the HH Subband for X-rays, MRI and CT scan modalities. |
4.5. Comparative Comparsion With Other Approaches
We have presented Table 1 to compare the performance of our approach with two approaches in the literature. We have noticed that in the LL suband, our approach outperforms other research works in the references [1A.K. Gupta, and M.S. Raval, "A robust and secure watermarking scheme based on singular values replacement", Sadhana, vol. 37, no. 4, pp. 425-440.
[http://dx.doi.org/10.1007/s12046-012-0089-x] , 16G. Emir, and A. Eskicioglu, "Robust DWT-SVD domain image watermarking: embedding data in all frequencies", Proceedings of the ACM 2004 Workshop on Multimedia and Security., .] for different listed attacks. In addition, we observed that the proposed approach exceeds other approaches for (LH, HL and HH) subands in terms of providing higher NC measure values. Hence, we can say that our approach is better those two approaches in all subands for various kinds of attacks listed in table below.
 |
Fig. (8) Recovered hospital watermark logo from medical image after different kinds of attacks. |
 |
Fig. (9) Recovered hospital watermark logo from medical image after four kinds of attacks at seven DWT decomposition levels. |
CONCLUSION
We have presented in this research paper an approach to adjust automatically the number of selected subands to embed the diagonal coefficients of watermark logos in the cover medical image. The criteria of adjustment (or adaptation) depends on the size of cover image and watermark logo. The maximum number of decomposition levels for embedding is determined by seven levels. We concluded that the effects of applied attacks might be different for each modality and each suband of cover image. For instance, the images produced by CT modality have more resistance to the noise and compression attacks in the higher decomposition subands while the X-rays and MRI images are more resistant to the mean and median attacks. However, generally, the noise attack is the most influential attack on all images produced by all modalities, and the contrast attack is the least (or no effect) attack on the different kinds of images. Furthermore, the geometric attacks (i.e. rotate and shear) have an adverse effects on the performance of medical multimedia systems. In the future, we will use other transforms such as DCT and cryptographic algorithms to enhance the security of healthcare systems.
CONSENT FOR PUBLICATION
Not applicable.
CONFLICT OF INTEREST
The authors declare no conflict of interest, financial or otherwise.
ACKNOWLEDGEMENTS
Declared none.
REFERENCES
| [1] | A.K. Gupta, and M.S. Raval, "A robust and secure watermarking scheme based on singular values replacement", Sadhana, vol. 37, no. 4, pp. 425-440. [http://dx.doi.org/10.1007/s12046-012-0089-x] |
| [2] | A. Zear, A.K. Singh, and P. Kumar, "A proposed secure multiple watermarking technique based on DWT, DCT and SVD for application in medicine", Multimedia Tools Appl., vol. 77, no. 4, pp. 4863-4882. [http://dx.doi.org/10.1007/s11042-016-3862-8] |
| [3] | A. Al-Haj, and A. Amer, "Secured telemedicine using region-based watermarking with tamper localization", J. Digit. Imaging, vol. 27, no. 6, pp. 737-750. [http://dx.doi.org/10.1007/s10278-014-9709-9] [PMID: 24874408] |
| [4] | A. Al-Haj, G. Abandah, and N. Hussien, "Crypto-based algorithms for secured medical image transmission", IET Inf. Secur., vol. 9, no. 6, pp. 365-373. [http://dx.doi.org/10.1049/iet-ifs.2014.0245] |
| [5] | R. Eswaraiah, and E.S. Reddy, "Robust medical image watermarking technique for accurate detection of tampers inside region of interest and recovering original region of interest", IET Image Process., vol. 9, no. 8, pp. 615-625. [http://dx.doi.org/10.1049/iet-ipr.2014.0986] |
| [6] | A.J. Abboud, A.N. Albu-Rghaif, and A.K. Jassim, "Balancing compression and encryption of satellite imagery", Iran. J. Electr. Comput. Eng., vol. 8, no. 5, pp. 3568-3586. |
| [7] | H. Al-Assam, A.J. Abboud, and S.A. Jassim, "Hidden assumption of face recognition evaluation under different quality conditions"", IEEE International Conference on Information Society (i-Society), England., . |
| [8] | S. Bravo-Solorio, F. Calderon, C-T. Li, and A.K. Nandi, "Fast fragile watermark embedding and iterative mechanism with high self-restoration performance", Digital Signal Processing, vol. 73, pp. 83-92. [http://dx.doi.org/10.1016/j.dsp.2017.11.005] |
| [9] | P. Dong, J.G. Brankov, N.P. Galatsanos, Y. Yang, and F. Davoine, "Digital watermarking robust to geometric distortions", IEEE Trans. Image Process., vol. 14, no. 12, pp. 2140-2150. [http://dx.doi.org/10.1109/TIP.2005.857263] [PMID: 16370466] |
| [10] | A. Al-Haj, "Combined DWT-DCT digital image watermarking", J. Comput. Sci., vol. 3, no. 9, pp. 740-746. [http://dx.doi.org/10.3844/jcssp.2007.740.746] |
| [11] | A.J. Abboud, and S.A. Jassim, "Incremental fusion of partial biometric information", Mobile Multimedia/Image Processing, Security, and Applications 2012 by International Society for Optics and Photonics, vol. Vol. 8406, . [http://dx.doi.org/10.1117/12.918776] |
| [12] | A.J. Abboud, and S.A. Jassim, "Image quality guided approach for adaptive modelling of biometric intra-class variations", 2010 Proceedings of SPIE - The International Society for Optical Engineering, . [http://dx.doi.org/10.1117/12.850592] |
| [13] | A. Kahate, Cryptography and network security., McGraw-Hill Education, . |
| [14] | A.N. Albu-Rghaif, A.K. Jassim, and A.J. Abboud, "A data structure encryption algorithm based on circular queue to enhance data security", Engineering Sciences-3rd Scientific Conference of Engineering Science (ISCES), 2018 1st International Scientific Conference of. IEEE, Baqubah, . [http://dx.doi.org/10.1109/ISCES.2018.8340522] |
| [15] | Z. Wang, A.C. Bovik, H.R. Sheikh, and E.P. Simoncelli, "Image quality assessment: from error visibility to structural similarity", IEEE Trans. Image Process., vol. 13, no. 4, pp. 600-612. [http://dx.doi.org/10.1109/TIP.2003.819861] [PMID: 15376593] |
| [16] | G. Emir, and A. Eskicioglu, "Robust DWT-SVD domain image watermarking: embedding data in all frequencies", Proceedings of the ACM 2004 Workshop on Multimedia and Security., . |